您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
HAProxy 高級應用
================================================================================
概述:
本章將繼續上章的內容介紹haprosy代理配置段的相關參數,具體如下:
ACL控制訪問列表;
4層檢測機制:dst,dst_port,src,src_port
7層檢查機制:path、req.hdr、res.hdr;
http層訪問控制相關的參數:
block,http-request
TCP層的訪問控制參數
================================================================================
10.修改請求或響應報文首部相關:
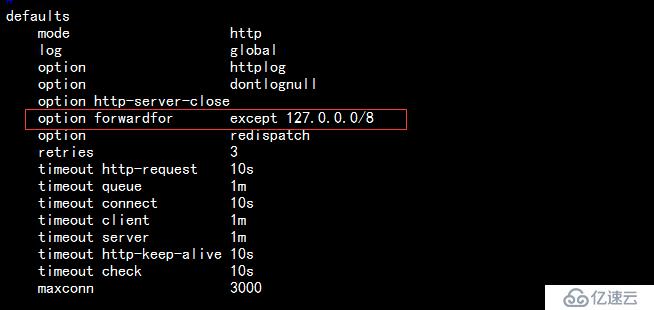
★option forwardfor [ except <network> ] [ header <name> ] [ if-none ]
⊙作用:
AProxy把請求報文發往后端主機之前在請求報文添加“X-Forwared-For”首部;其值為客戶端地址,
⊙范圍:都可以使用
⊙參數:
[ except <network> ]:除了xxx不添加外,如從本地訪問
[ header <name> ]:可以自定義首部名稱;
[ if-none ]:沒有首部時才添加
Examples :
# Public HTTP address also used by stunnel on the same machine frontend www mode http option forwardfor except 127.0.0.1 # stunnel already adds the header # Those servers want the IP Address in X-Client backend www mode http option forwardfor header X-Client★添加或刪除請求,響應報文的首部
⊙reqadd <string> [{if | unless} <cond>]
在請求報文添加一個首部信息
⊙rspadd <string> [{if | unless} <cond>]
在響應報文添加一個首部信息
⊙reqdel <search> [{if | unless} <cond>]
reqidel <search> [{if | unless} <cond>] (ignore case)忽略大小寫
刪除請求報文首部
⊙rspdel <search> [{if | unless} <cond>]
rspidel <search> [{if | unless} <cond>] (ignore case)
刪除響應報文首部
注意:
添加或者刪除請求響應報文首部的參數的使用范圍是frontend、listen和backend
演示1:HAProxy把請求報文發往后端主機之前在請求報文添加“X-Forwared-For”首部;
1.首先編輯haproxy的配置文件,定義除了本機之外,所有的請求報文均添加X-Forwared-For,首部記錄客戶端信息發往后端主機,如下:
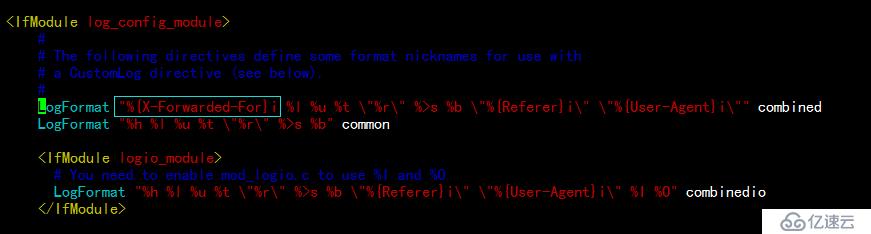
2.編輯后端主機RS1的httpd服務的配置文件/etc/httpd/conf/httpd.conf,修改日志的格式,如下:
3.在啟動RS1后端主機,在瀏覽器中訪問,在RS1中查看日志,可以看到記錄的日志為用戶遠端地址,而非haproxy的代理地址;
[root@centos7 ~]# tail -5 /var/log/httpd/access_log 192.168.1.105 - - [21/Nov/2016:23:48:54 +0800] "GET / HTTP/1.1" 304 - "-" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.116 Safari/537.36" 192.168.1.105 - - [21/Nov/2016:23:49:39 +0800] "GET / HTTP/1.1" 304 - "-" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.116 Safari/537.36" 192.168.1.105 - - [21/Nov/2016:23:50:29 +0800] "GET / HTTP/1.1" 304 - "-" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.116 Safari/537.36" 192.168.1.105 - - [21/Nov/2016:23:50:30 +0800] "GET / HTTP/1.1" 304 - "-" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.116 Safari/537.36" 192.168.1.105 - - [21/Nov/2016:23:50:30 +0800] "GET / HTTP/1.1" 304 - "-" "Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/53.0.2785.116 Safari/537.36"
------------------------------------------------------------------------------------------
演示2:
1.添加響應客戶端報文的首部為經由haproxy轉發的首部信息,如下:
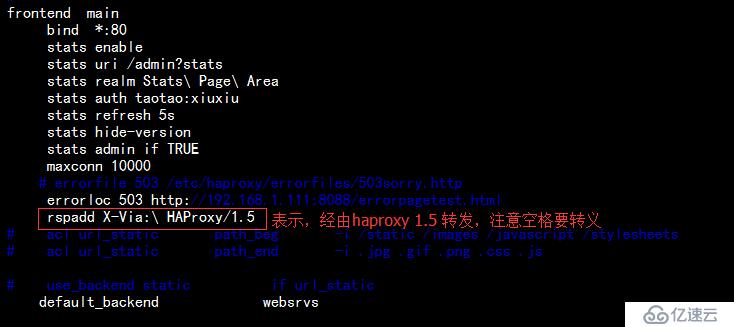
重載haproxy服務,請求查看首部信息如下:
[root@centos7 ~]# curl -I http://192.168.1.111 HTTP/1.1 200 OK Date: Mon, 21 Nov 2016 16:31:02 GMT Server: Apache/2.4.6 (CentOS) PHP/5.4.16 Last-Modified: Fri, 18 Nov 2016 16:09:35 GMT ETag: "1a-54195883a68b2" Accept-Ranges: bytes Content-Length: 26 Content-Type: text/html; charset=UTF-8 X-Via: HAProxy/1.5
2.刪除響應首部信息Server,編輯配置文件如下:
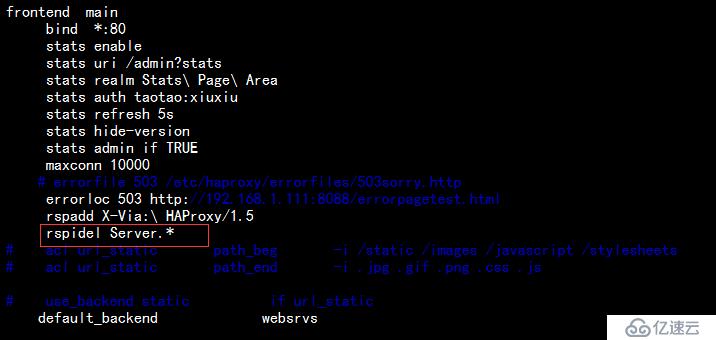
重載haproxy服務,請求查看首部信息,發現已經刪除了Server的首部,如下:
[root@centos7 ~]# curl -I http://192.168.1.111 HTTP/1.1 200 OK Date: Mon, 21 Nov 2016 16:33:59 GMT Last-Modified: Fri, 18 Nov 2016 16:09:35 GMT ETag: "1a-54195883a68b2" Accept-Ranges: bytes Content-Length: 26 Content-Type: text/html; charset=UTF-8 X-Via: HAProxy/1.5
11.超時時長:
★timeout client <timeout>:
作用:設置客戶端連接最大非活動時長,默認單位是毫秒;
★timeout server <timeout>
作用:設置服務端連接最大非活動時長,默認單位是毫秒;
★timeout connect <timeout>
作用:向服務端建立連接時的超時時長;
★timeout http-keep-alive <timeout>
作用:面向客戶端一側啟用保持連接功能的超時時長,默認單位為ms;
★timeout client-fin <timeout>
作用:客戶端一側的半連接超時時長;
★timeout server-fin <timeout>
作用:服務端一側的半連接超時時長;
12.ACL控制訪問列表
★語法格式:
acl <aclname> <criterion> [flags] [operator] [<value>] ...
⊙<aclname>:
ACL names must be formed from upper and lower case letters, digits, '-' (dash), '_' (underscore) , '.' (dot) and ':' (colon). ACL names are case-sensitive. ACL名稱可由,大小寫字母,數字,'-','_','.'和':' 并且區分大小寫。
⊙<value>的類型:
- boolean //布爾型值
- integer or integer range //整數或整數范圍
- IP address / network //ip地址
- string (exact, substring, suffix, prefix, subdir, domain) //字符串
- regular expression //正則表達式
- hex block
⊙[flags]
-i : 被模式匹配時忽略字符大小寫,比較常用
-f : load patterns from a file.
-m : use a specific pattern matching method
-n : forbid the DNS resolutions
-M : load the file pointed by -f like a map file.
-u : force the unique id of the ACL
-- : force end of flags. Useful when a string looks like one of the flags. //轉義
⊙[operator]
◆數值匹配:
eq : true if the tested value equals at least one value
ge : true if the tested value is greater than or equal to at least one value
gt : true if the tested value is greater than at least one value
le : true if the tested value is less than or equal to at least one value
lt : true if the tested value is less than at least one value
◆字符串匹配:
- exact match (-m str) : 字符串精確匹配
- substring match (-m sub) : 子串匹配
- prefix match (-m beg) : 前綴匹配
- suffix match (-m end) : 后綴匹配
- subdir match (-m dir) : 子目錄匹配
- domain match (-m dom) : 域匹配
⊙條件的邏輯連接
- AND (implicit)
- OR (explicit with the "or" keyword or the "||" operator)
- Negation with the exclamation mark ("!")
★<creterion>:
⊙4層檢測機制:
dst : ip
dst_port : integer
src : ip
src_port : integer
⊙block { if | unless } <condition>
作用:條件匹配就阻斷一個7層請求
Example:
acl invalid_src src 0.0.0.0/7 224.0.0.0/3 acl invalid_src src_port 0:1023 acl local_dst hdr(host) -i localhost block if invalid_src || local_dst
演示:
1.阻斷來自非 10.1.250.25 的ip(瀏覽器地址)請求,編輯配置文件,如下:
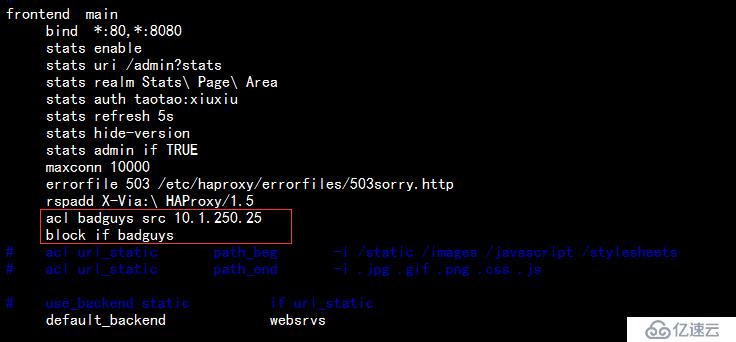
重載haproxy服務,在瀏覽器中訪問可以發現,拒絕訪問
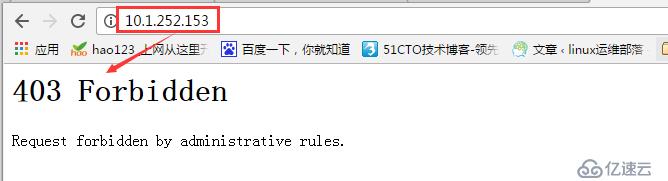
在本機使用curl命令可以正常訪問,說明僅拒絕了來自10.1.250.25的ip的請求。
[root@centos7 haproxy]# curl http://10.1.252.153 <h2>Backend Server 1</h2> [root@centos7 haproxy]# curl http://10.1.252.153 <h2>Backend Server 1</h2> [root@centos7 haproxy]# curl http://10.1.252.153 <h2>Backend Server 2</h2>
-------------------------------------------------------------------------------------------
2.僅允許本瀏覽器(10.1.250.25)可以訪問8080端口,編輯配置文件如下:
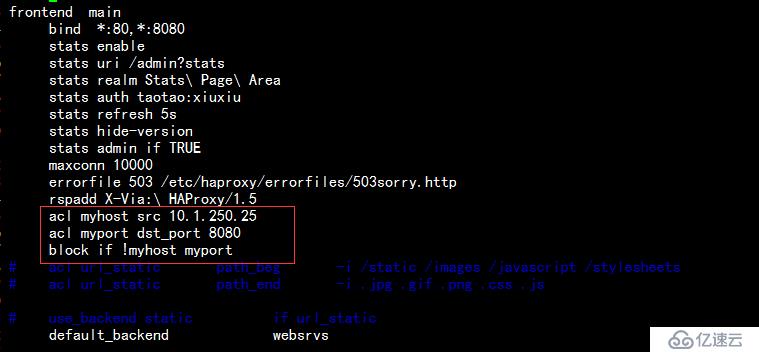
重載haproxy服務,在瀏覽器中訪問可以發現,可以正常訪問

在本機使用curl命令訪問8080端口,拒絕訪問,如下:
[root@centos7 haproxy]# curl http://10.1.252.153:8080 <html><body><h2>403 Forbidden</h2> Request forbidden by administrative rules. </body></html>
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。