您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
一、簡介
1、獲取更多的NSClient原理,請參考NSClient++官方站點
NSClient++官網:http://www.nsclient.org/
2、NSClient++與NRPE
NSClient++的工作原理
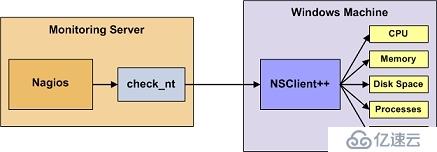
NRPE的工作原理
Nagios對Windows主機的監控主要有三種方法
第一種是NSclient++
第二種是NRPE
第三種是SNMP(不是很常用)
NSclient++與nrpe最大的區別就是:
1、被監控機上安裝有nrpe,并且還有插件,最終的監控是由這些插件來進行的.當監控主機將監控請求發給nrpe后,nrpe調用插件來完成監控.
2、NSclient++則不同,被監控機上只安裝NSclient++,沒有任何的插件.當監控主機將監控請求發給NSclient++后,NSclient++直接完成監控,所有的監控是由NSclient++完成的。
這也說明了NSclient++的一個很大的問題,不靈活,沒有可擴展性.它只能完成自己本身包含的監控操作,不能由一些插件來擴展.好在NSclient++已經做的不錯了,基本上可以完全滿足我們的監控需要。
二、check_nt的方式監控windows主機
1、下載NSClient++
下載地址:http://sourceforge.net/projects/nscplus/files/nscplus/
2、安裝NSClient++

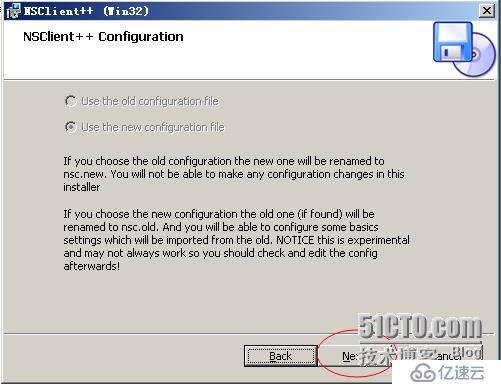
Allowed hosts:(this is the IP of the nagios (or other)server)
允許的主機地址:Nagios服務器端的IP地址
NSClient password(only userd via check_nt)
NSClient的密碼:填寫Nagios跟NSClient++進程通信的密碼,可以不設置
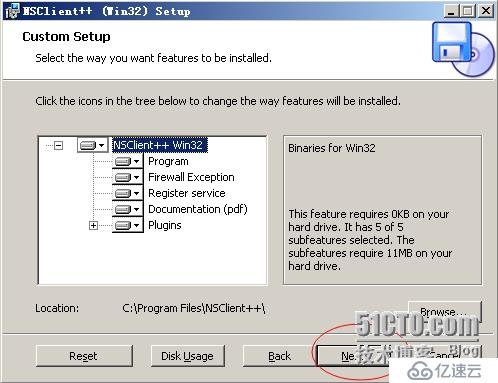
Modules to load:
安裝并加載相應的模塊:NSClient++自帶的有check_plugins插件,check_nt,check_nrpe,NSCA,WMI
在這里我們全部選擇,以后會有用到的。
點擊【Finsh】,表示安裝NSClient++完成
3、查看NSClient++服務是否已經啟用
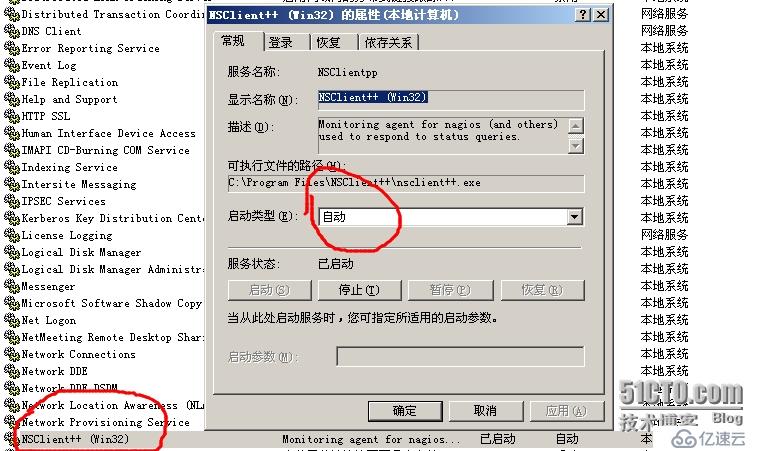
4、查看NSClient++的配置文件
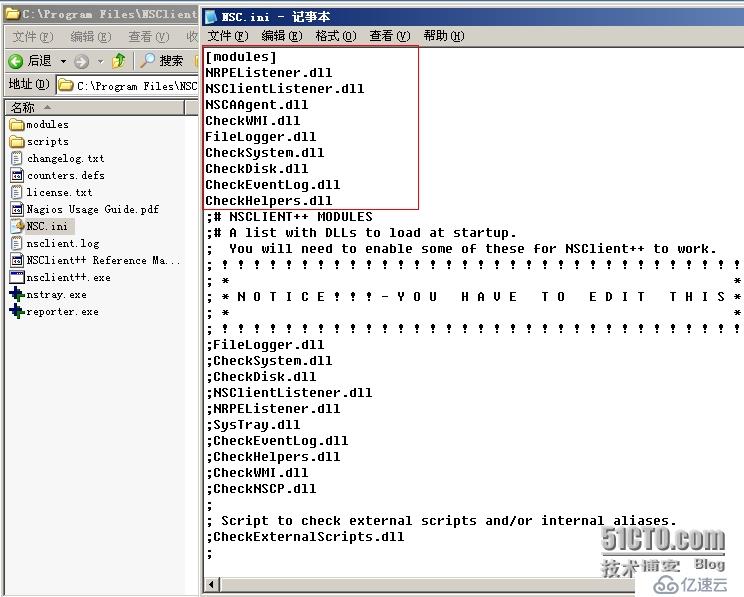
默認是安裝在C:\Program Files\NSClient++ 目錄下,NSC.ini即為NSClient服務的配置文件,一般我們無需修改,但是當我們監控端的IP地址改變時,或者密碼忘記,即可以在這里修改了。
安裝時加載的模塊
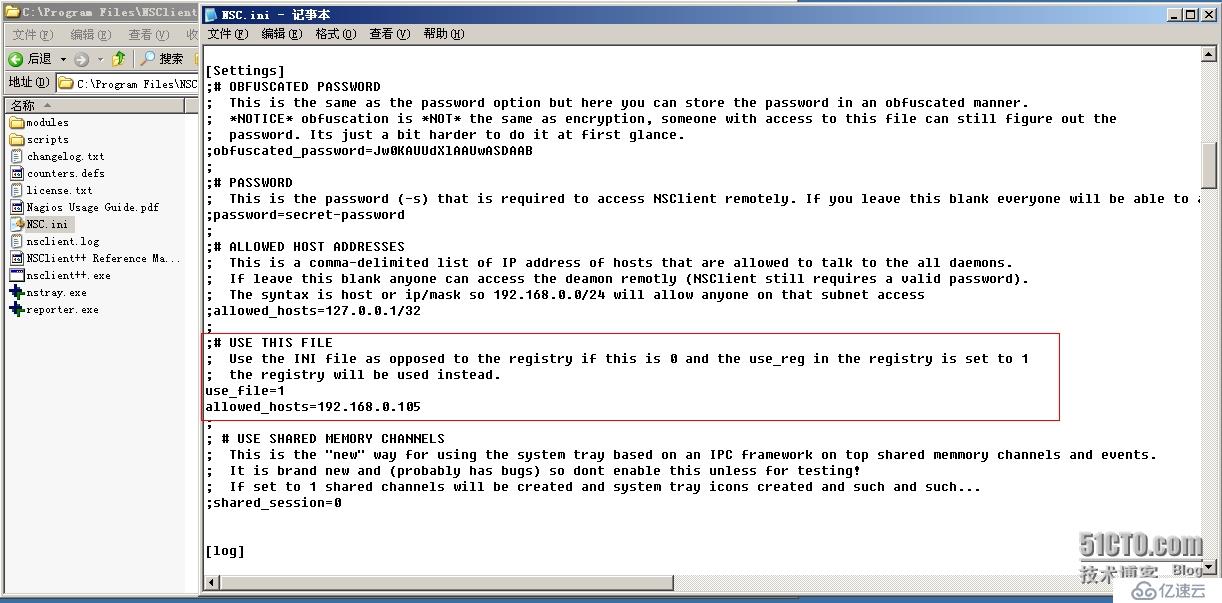
設置允許連接的地址:為Nagios的IP地址
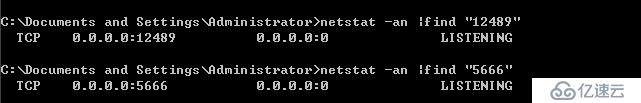
NRPE的默認端口號
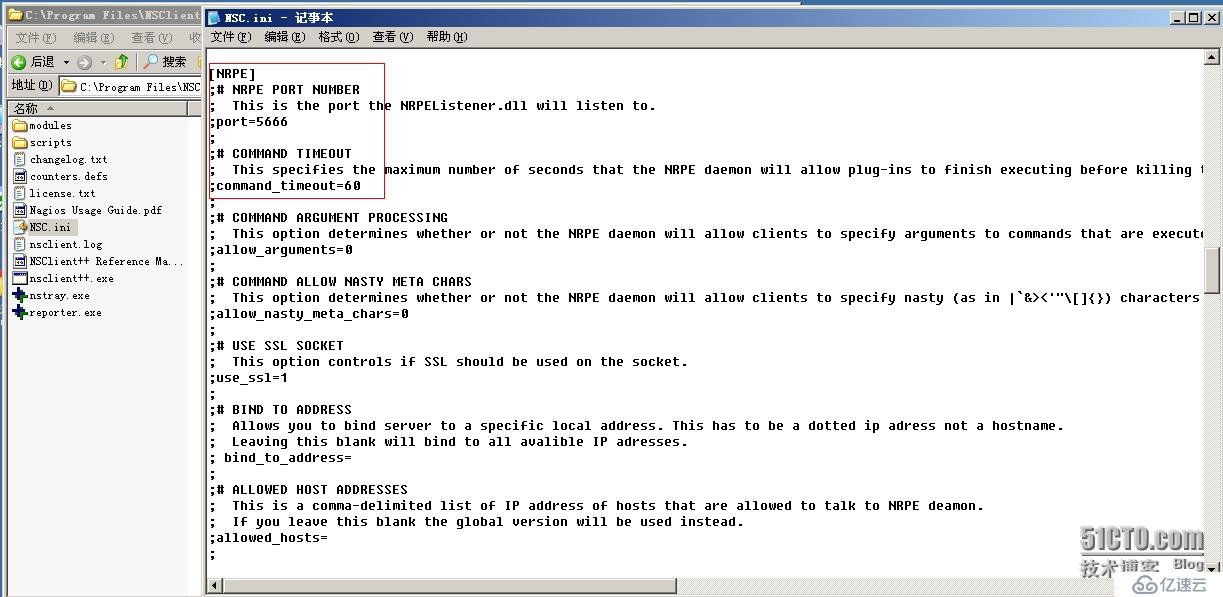
三、NSClient應用監控
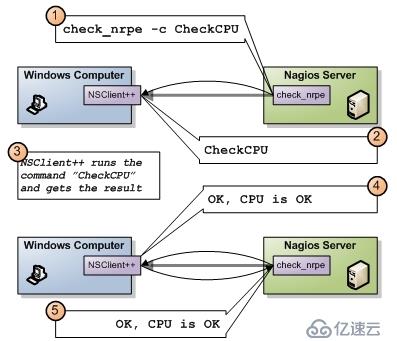
NSClient++與Nagios服務器通信,主要使用Nagios服務器的check_nt插件。原理圖如下
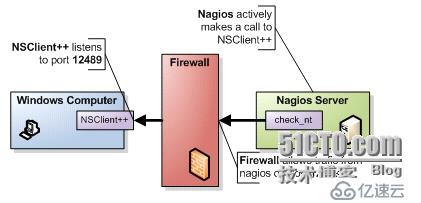
1、check_nt插件的使用說明
[root@Nagios ~]# cd /usr/local/nagios/libexec/
[root@Nagios libexec]# ./check_nt -h #查看check_nt的語法
check_nt v2.0.3 (nagios-plugins 2.0.3)
Copyright (c) 2000 Yves Rubin (rubiyz@yahoo.com)
Copyright (c) 2000-2014 Nagios Plugin Development Team
<devel@nagios-plugins.org>
This plugin collects data from the NSClient service running on a
Windows NT/2000/XP/2003 server.
Usage:
check_nt -H host -v variable [-p port] [-w warning] [-c critical]
[-l params] [-d SHOWALL] [-u] [-t timeout]
Options:
-h, --help
Print detailed help screen
-V, --version
Print version information
--extra-opts=[section][@file]
Read options from an ini file. See
https://www.nagios-plugins.org/doc/extra-opts.html
for usage and examples.
Options:
-H, --hostname=HOST
Name of the host to check
-p, --port=INTEGER
Optional port number (default: 1248) #默認端口號
-s, --secret=<password> #指定的密碼
Password needed for the request
-w, --warning=INTEGER
Threshold which will result in a warning status
-c, --critical=INTEGER
Threshold which will result in a critical status
-t, --timeout=INTEGER
Seconds before connection attempt times out (default: -l, --params=<parameters>
Parameters passed to specified check (see below) -d, --display={SHOWALL}
Display options (currently only SHOWALL works) -u, --unknown-timeout
Return UNKNOWN on timeouts10)
-h, --help
Print this help screen
-V, --version
Print version information
-v, --variable=STRING
Variable to check
Valid variables are:
CLIENTVERSION = Get the NSClient version
If -l <version> is specified, will return warning if versions differ.
CPULOAD =
Average CPU load on last x minutes.
Request a -l parameter with the following syntax:
-l <minutes range>,<warning threshold>,<critical threshold>.
<minute range> should be less than 24*60.
Thresholds are percentage and up to 10 requests can be done in one shot.
ie: -l 60,90,95,120,90,95
UPTIME =
Get the uptime of the machine.
-l <unit>
<unit> = seconds, minutes, hours, or days. (default: minutes)
Thresholds will use the unit specified above.
USEDDISKSPACE =
Size and percentage of disk use.
Request a -l parameter containing the drive letter only.
Warning and critical thresholds can be specified with -w and -c.
MEMUSE =
Memory use.
Warning and critical thresholds can be specified with -w and -c.
SERVICESTATE =
Check the state of one or several services.
Request a -l parameters with the following syntax:
-l <service1>,<service2>,<service3>,...
You can specify -d SHOWALL in case you want to see working services
in the returned string.
PROCSTATE =
Check if one or several process are running.
Same syntax as SERVICESTATE.
COUNTER =
Check any performance counter of Windows NT/2000.
Request a -l parameters with the following syntax:
-l "\\<performance object>\\counter","<description>
The <description> parameter is optional and is given to a printf
output command which requires a float parameter.
If <description> does not include "%%", it is used as a label.
Some examples:
"Paging file usage is %%.2f %%%%"
"%%.f %%%% paging file used."
INSTANCES =
Check any performance counter object of Windows NT/2000.
Syntax: check_nt -H <hostname> -p <port> -v INSTANCES -l <counter object>
<counter object> is a Windows Perfmon Counter object (eg. Process),
if it is two words, it should be enclosed in quotes
The returned results will be a comma-separated list of instances on
the selected computer for that object.
The purpose of this is to be run from command line to determine what instances
are available for monitoring without having to log onto the Windows server
to run Perfmon directly.
It can also be used in scripts that automatically create Nagios service
configuration files.
Some examples:
check_nt -H 192.168.1.1 -p 1248 -v INSTANCES -l Process #check_nt的語法
Notes:
- The NSClient service should be running on the server to get any information
(http://nsclient.ready2run.nl).
- Critical thresholds should be lower than warning thresholds
- Default port 1248 is sometimes in use by other services. The error
output when this happens contains "Cannot map xxxxx to protocol number".
One fix for this is to change the port to something else on check_nt
and on the client service it's connecting to.
Send email to help@nagios-plugins.org if you have questions regarding use
of this software. To submit patches or suggest improvements, send email to
devel@nagios-plugins.org2、check_nt命令的使用
check_nt參數解釋
-w:警告比例
-c:緊急比例
-l:過去5分鐘的平均值,80%的警告 90%緊急
四、定義命令、主機、服務
1、定義命令
[root@Nagios ~]# vim /usr/local/nagios/etc/objects/commands.cfg
# 'check_win' command definition
define command{
command_name check_win
command_line $USER1$/check_nt -H $HOSTADDRESS$ -p 12489 -v $ARG1$ $ARG2$
}
注釋:
$..$ 表示系統內置的宏,也就是所謂的變量
$USER1$ 表示插件所在的目錄
-H 指定主機地址
$HOSTADDRESS$ 應用到哪個主機,就用哪個主機的地址
$ARG1$ 傳遞的參數,形參
-s 指定密碼 默認為空2、定義主機和服務
[root@Nagios objects]# cp windows.cfg windows106.cfg [root@Nagios objects]# sed -i 's/winserver/Windows106/g' windows106.cfg [root@Nagios objects]# sed -i 's/192.168.1.2/192.168.0.106/' windows106.cfg
4、檢測配置文件是否有語法錯誤
[root@Nagios ~]# service nagios configtest Nagios Core 4.0.7 Copyright (c) 2009-present Nagios Core Development Team and Community Contributors Copyright (c) 1999-2009 Ethan Galstad Last Modified: 06-03-2014 License: GPL Website: http://www.nagios.org Reading configuration data... Read main config file okay... Read object config files okay... Running pre-flight check on configuration data... Checking objects... Checked 8 services. Checked 1 hosts. Checked 1 host groups. Checked 0 service groups. Checked 1 contacts. Checked 1 contact groups. Checked 25 commands. Checked 5 time periods. Checked 0 host escalations. Checked 0 service escalations. Checking for circular paths... Checked 1 hosts Checked 0 service dependencies Checked 0 host dependencies Checked 5 timeperiods Checking global event handlers... Checking obsessive compulsive processor commands... Checking misc settings... Total Warnings: 0 Total Errors: 0 Things look okay - No serious problems were detected during the pre-flight check Object precache file created: /usr/local/nagios/var/objects.precache
5、重啟nagios服務
[root@Nagios objects]# service nagios restart Running configuration check... Stopping nagios: .done. Starting nagios: done.
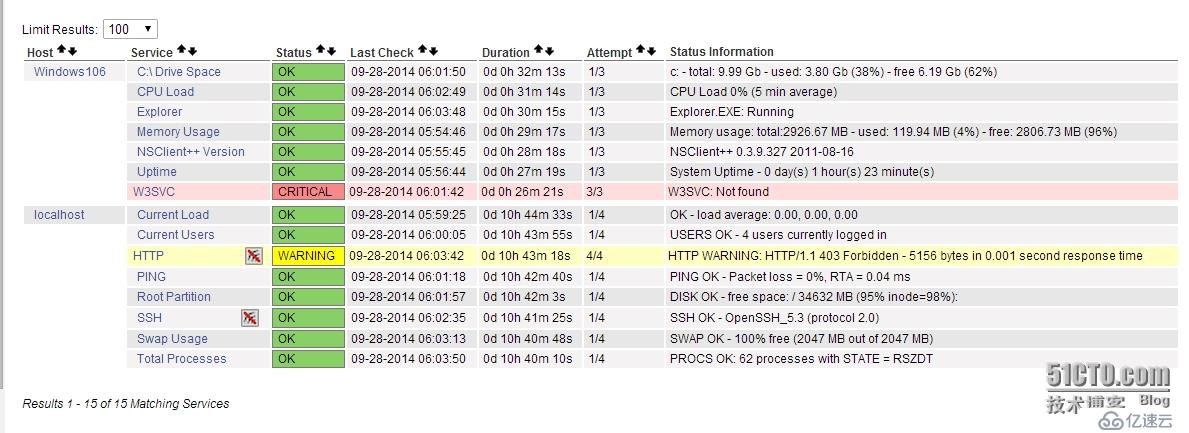
四、瀏覽器查看監控信息
1、登陸后點擊【Hosts】,查看新監控的Windows主機信息

2、點擊【Services】,查看Windows服務的狀態信息
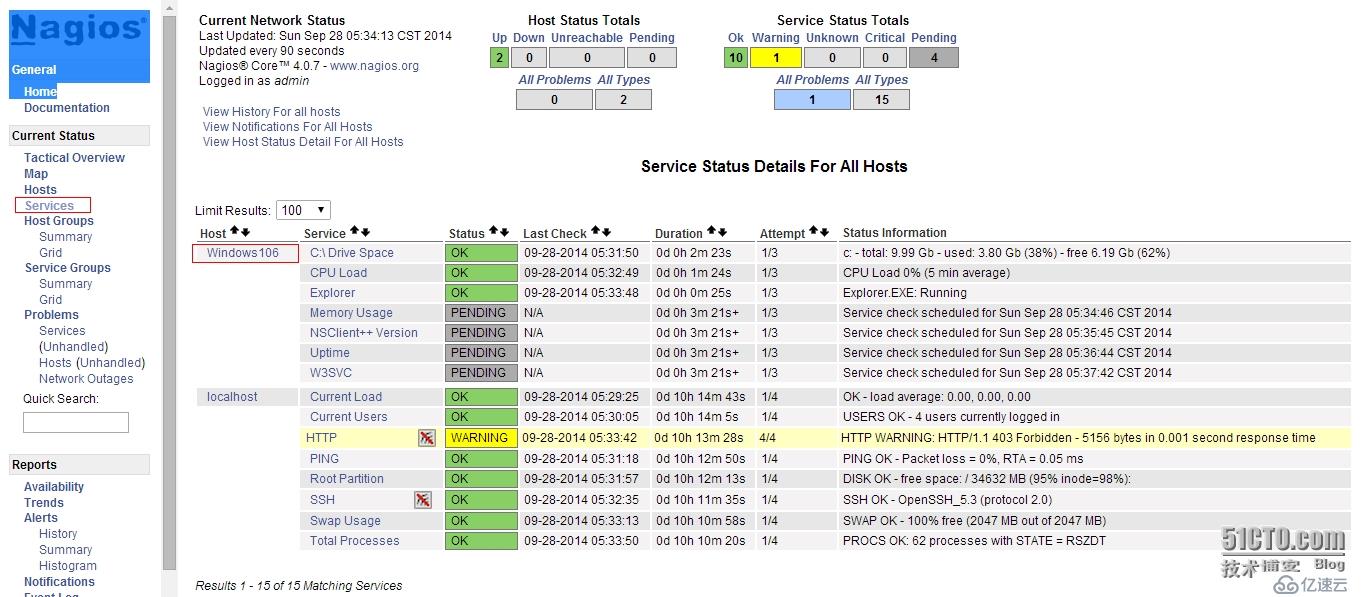
3、等待幾分鐘后狀態就正常了,如下圖所示
三、NRPE的方式監控windows主機
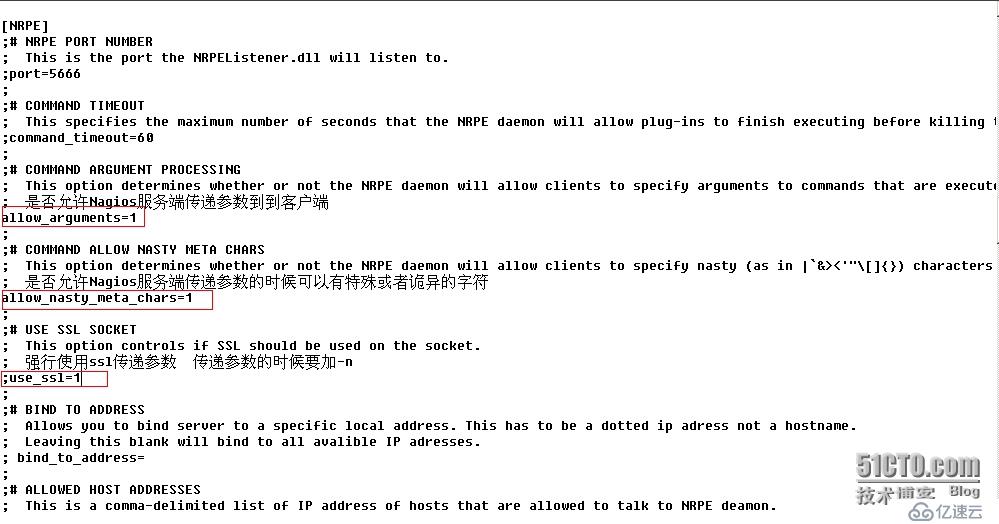
1、修改NSClient++的配置文件
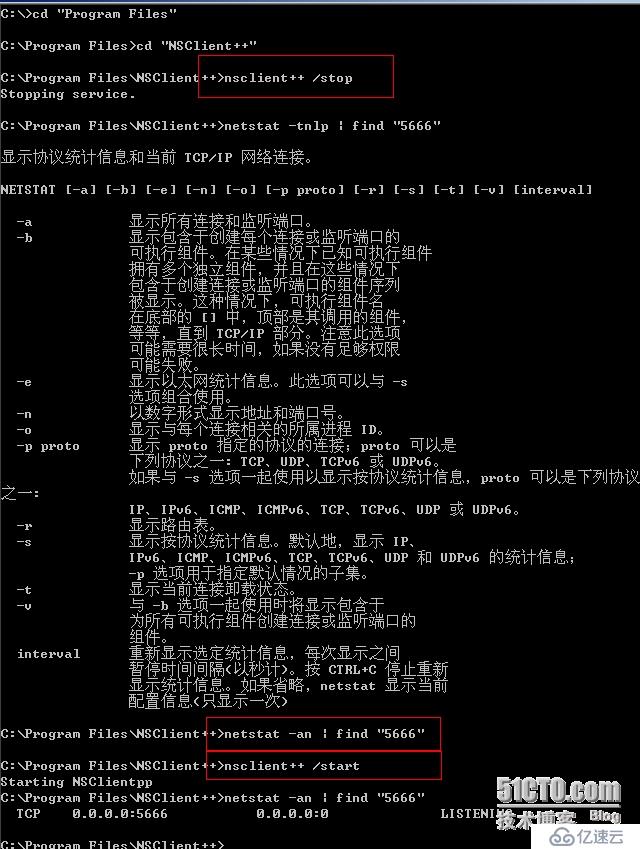
2、重新啟動NSClient++服務
3、Nagios服務端測試NRPE命令
[root@Nagios ~]# cd /usr/local/nagios/libexec/ [root@Nagios libexec]# ./check_nrpe -h NRPE Plugin for Nagios Copyright (c) 1999-2008 Ethan Galstad (nagios@nagios.org) Version: 2.15 Last Modified: 09-06-2013 License: GPL v2 with exemptions (-l for more info) SSL/TLS Available: Anonymous DH Mode, OpenSSL 0.9.6 or higher required Usage: check_nrpe -H <host> [ -b <bindaddr> ] [-4] [-6] [-n] [-u] [-p <port>] [-t <timeout>] [-c <command>] [-a <arglist...>] Options: -n = Do no use SSL -u = Make socket timeouts return an UNKNOWN state instead of CRITICAL <host> = The address of the host running the NRPE daemon <bindaddr> = bind to local address -4 = user ipv4 only -6 = user ipv6 only [port] = The port on which the daemon is running (default=5666) [timeout] = Number of seconds before connection times out (default=10) [command] = The name of the command that the remote daemon should run [arglist] = Optional arguments that should be passed to the command. Multiple arguments should be separated by a space. If provided, this must be the last option supplied on the command line. Note: This plugin requires that you have the NRPE daemon running on the remote host. You must also have configured the daemon to associate a specific plugin command with the [command] option you are specifying here. Upon receipt of the [command] argument, the NRPE daemon will run the appropriate plugin command and send the plugin output and return code back to *this* plugin. This allows you to execute plugins on remote hosts and 'fake' the results to make Nagios think the plugin is being run locally. check_nrpe語法: check_nrpe ... -c <command> [-a <argument> <argument> <argument>] check_nrpe的內置命令: · CheckAlwaysCRITICAL (check) · CheckAlwaysOK (check) · CheckAlwaysWARNING (check) · CheckCPU (check) · CheckCRITICAL (check) · CheckCounter (check) · CheckEventLog/CheckEventLog (check) · CheckFile (check) · CheckFileSize (check) · CheckMem (check) · CheckMultiple (check) · CheckOK (check) · CheckProcState (check) · CheckServiceState (check) · CheckTaskSched/CheckTaskSched (check) · CheckUpTime (check) · CheckVersion (check) · CheckWARNING (check) · CheckWMI/CheckWMI (check) · CheckWMIValue (check)
[root@Nagios libexec]# ./check_nrpe -H 192.168.1.142 -p 5666 -c CheckCPU -a warn=80 crit=90 time=20m time=10s time=4 OK CPU Load ok.|'20m'=0%;80;90 '10s'=0%;80;90 '4'=0%;80;90
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。