您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
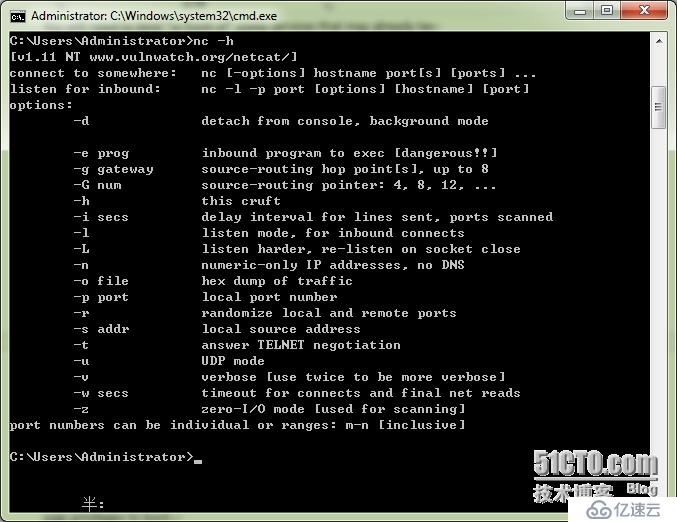
UPDATE 12/27/04security fix in -e option for Windows
Netcat 1.11 for NT- nc111nt.zip
The originalversion of Netcat was written by *hobbit* <hobbit@avian.org>
The NT version wasdone by Weld Pond <weld@vulnwatch.org>
Netcat for NT isthe tcp/ip "Swiss Army knife" that never made it into any
of the resourcekits. It has proved to be an extremelyversatile tool on
the unix platform.So why should NT always be unix's poor cousin when it
comes to tcp/iptesting and exploration? I bet many NTadmins out there
keep a unix boxaround to use tools such as Netcat or to test their systems
with the unixversion of an NT vulnerability exploit. With Netcat for NT
part of thatfeeling disempowerment is over.
Included with thisrelease is Hobbit's original description of the powers
of Netcat. In this document I will briefly describe someof the things an
NT admin mightwant to do and know about with Netcat on NT. For more
detailed technicalinformation please read hobbit.txt included in the
nc11nt.ziparchive.
Basic Features
* Outbound or inbound connections, TCP orUDP, to or from any ports
* Full DNS forward/reverse checking, withappropriate warnings
* Ability to use any local source port
* Ability to use any locally-configurednetwork source address
* Built-in port-scanning capabilities,with randomizer
* Can read command line arguments fromstandard input
* Slow-send mode, one line every N seconds
* Hex dump of transmitted and receiveddata
* Ability to let another program serviceestablished
connections
* Telnet-options responder
New for NT
* Ability to run in the background withouta console window
* Ability to restart as a single-threadedserver to handle a new
connection
A simple exampleof using Netcat is to pull down a web page from a web
server. With Netcat you get to see the full HTTPheader so you can see
which web server aparticular site is running.
Since NT has arather anemic command processor, some of the things that are
easy in unix maybe a bit more clunky in NT. For the web page example first
create a fileget.txt that contains the following line and then a blank
line:
GET / HTTP/1.0
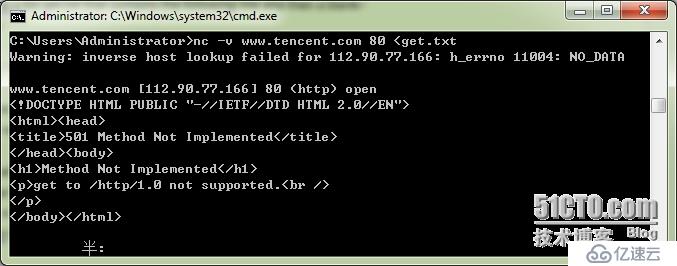
To use Netcat toretrieve the home page of a web site use the command:
nc -vwww.website.com 80 < get.txt
You will seeNetcat make a connection to port 80, send the text contained
in the fileget.txt, and then output the web server's response to stdout.
The -v is forverbose(冗長). It tells you a little info about the connection
when it starts.
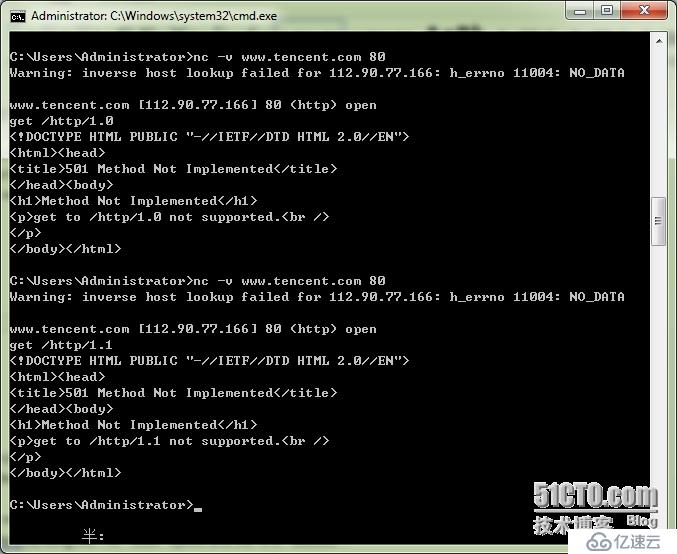
It is a bit easierto just open the connection and then type at the console
to do the samething.
nc -vwww.website.com 80
Then just type inGET / HTTP/1.0 and hit a couple of returns. You will
see the same thingas above.
A far more exciting thing to do is to get a quickshell going on a remote
machine by using the -l or "listen" optionand the -e or "execute"
option. You run Netcat listening onparticular port for a connection.
When a connectionis made, Netcat executes the program of your choice
and connects thestdin and stdout of the program to the network connection.
nc -l -p 23 -t -ecmd.exe
will get Netcat listeningon port 23 (telnet). When it getsconnected to
by a client itwill spawn產生 a shell (cmd.exe). The -t option tells Netcat
to handle anytelnet negotiation the client might expect.
This will allowyou to telnet to the machine you have Netcat listening on
and get a cmd.exeshell when you connect. You could justas well use
Netcat instead oftelnet:
nc xxx.xxx.xxx.xxx23
把nc當作服務器端,監聽指定端口,并且回應處理針對該端口的telnet連接
will get the jobdone. There is no authentication on thelistening side
so be a bit carefulhere. The shell is running with thepermissions of the
process thatstarted Netcat so be very careful. Ifyou were to use the
AT program toschedule Netcat to run listening on a port with the
-e cmd.exe option,when you connected you would get a shell with user
NTAUTHORITY\SYSTEM.
通過nc獲得的shell的權限與啟動nc的進程的權限一樣。那么啟動nc的是哪個進程呢?如何判斷?
The beauty ofNetcat really shines when you realize that you can get it
listening on ANYport doing the same thing. Do a littleexploring and
see if thefirewall you may be behind lets port 53 through. Run Netcat
listening behindthe firewall on port 53.
nc -L -p 53 -ecmd.exe
Then from outsidethe firewall connect to the listening machine:
nc -vxxx.xxx.xxx.xx 53
If you get acommand prompt then you are executing commands on the
listeningmachine. Use 'exit' at the commandprompt for a clean
disconnect. The -L (note the capital L) option will restart Netcat with
the samecommand line when the connection is terminated. This way you can
connectover and over to the same Netcat process.
A new feature forthe NT version is the -d or detach分離 from console flag.
This will letNetcat run without an ugly console window cluttering up the
screen or showingup in the task list.
You can even getNetcat to listen on the NETBIOS ports that are probably
running on most NTmachines. This way you can get aconnection to a
machine that mayhave port filtering enabled in the TCP/IP Security Network
controlpanel. Unlike Unix, NT does not seem tohave any security around
which ports thatuser programs are allowed to bind to. This means any
user can run aprogram that will bind to the NETBIOS ports.
You will need tobind "in front of" some services that may already be
listening on thoseports. An example is the NETBIOS SessionService that
is running on port139 of NT machines that are sharing files. You need
to bind to aspecific source address (one of the IP addresses of the
machine) toaccomplish this. This gives Netcat priorityover the NETBIOS
service which is at a lowerpriority because it is bound to ANY IP address.
This is done withthe Netcat -s option:
nc -v -L -ecmd.exe -p 139 -s xxx.xxx.xxx.xxx
Now you canconnect to the machine on port 139 and Netcat will field
the connectionbefore NETBIOS does. You have effectivelyshut off
file sharing onthis machine by the way. You have donethis with just
user privileges toboot.
將nc綁定在一個已經正常使用中的端口上,但是這需要指定服務器的IP來提高nc的優先級,實質上是搶占了該端口的功能。之前的該端口的正常功能將不能再使用。
PROBLEMS withNetcat 1.1 for NT
There are a fewknown problems that will eventually be fixed. One is
the -w or timeoutoption. This works for final net readsbut not
forconnections. Another problem is usingthe -e option in UDP mode.
You may find thatsome of the features work on Windows 95. Most
of the listeningfeatures will not work on Windows 95 however. These will
be fixed in alater release.
Netcat isdistributed with full source code so that people can build
upon thiswork. If you add something useful ordiscover something
interesting aboutNT TCP/IP let met know.
Weld Pond<weld@l0pht.com>, 2/2/98
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。