您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
這篇文章給大家介紹現有CDP-DC集群怎么啟用Auto-TLS,內容非常詳細,感興趣的小伙伴們可以參考借鑒,希望對大家能有所幫助。
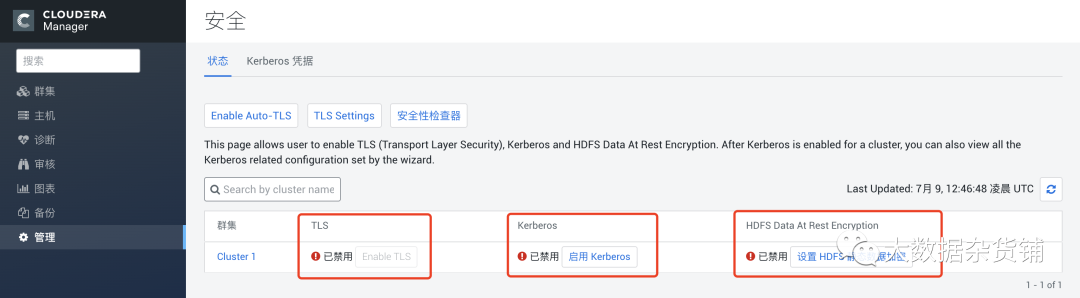
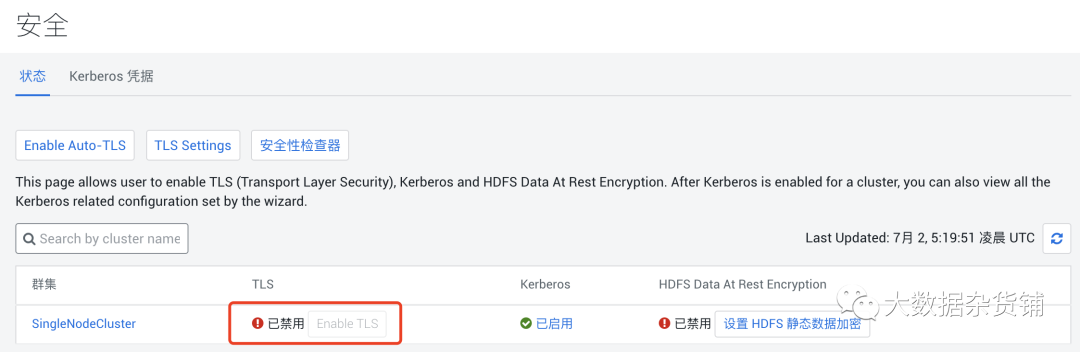
級別1(好) - 此級別僅配置瀏覽器和ClouderaManager之間以及代理和ClouderaManager服務器之間的加密通信。請參閱僅為Cloudera Manager配置TLS加密,然后按照級別1:為Cloudera Manager代理配置TLS加密,以獲取說明。 1級加密可以防止對代理和Cloudera Manager之間的通信進行窺探。
級別2(更好) - 此級別包括代理和服務器之間的加密通信,以及代理對Cloudera Manager服務器證書的強大驗證。請參閱第2級:由代理配置ClouderaManager服務器的TLS驗證。級別2通過驗證由Cloudera Manager服務器提供的證書的信任,為代理提供額外的安全級別。
級別3(最佳) - 代理和服務器之間的加密通信。3級TLS包括代理和服務器之間的加密通信,由代理對Cloudera Manager服務器證書進行強大的驗證,并使用自簽名或CA簽名的證書將代理驗證到Cloudera Manager服務器。請參閱第3級:將代理的TLS驗證配置到Cloudera Manager服務器。級別3解決了不受信任的網絡場景,您需要防止群集服務器被主機上運行的不受信任的代理人欺騙。 Cloudera建議您在啟用Kerberos身份驗證之前,為不受信任的網絡環境配置3級TLS加密。這提供了Cloudera Manager服務器和集群中經過驗證的代理之間的keytab的安全通信。
/usr/java/jdk1.8.0_232-cloudera/bin/jre/lib/security
export JAVA_HOME=/usr/java/jdk1.8.0_232-cloudera
export PATH=$JAVA_HOME/bin:$PATH
mkdir -p /opt/cloudera/security/x509/ /opt/cloudera/security/jks/

sudo chown -R cloudera-scm:cloudera-scm /opt/cloudera/security/jkssudo umask 0700cd /opt/cloudera/security/jks

keytool -genkeypair -alias cmhost -keyalg RSA -keysize 2048 -dname "cn=cm01.example.com, ou=Department,o=Company, l=City, st=State, c=US" -keypass password -keystore example.jks -storepass password
[root@ip-10-0-0-168 jks]# keytool -genkeypair -alias cmhost -keyalg RSA -keysize 2048 -dname "cn=ap-southeast-1.compute.internal, ou=ipausers,> o=Cloudera, l=Shanghai, st=Shanghai, c=CN" -keypass cloudera -keystore example.jks -storepass clouderaWarning:The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using "keytool -importkeystore -srckeystore example.jks -destkeystore example.jks -deststoretype pkcs12".[root@ip-10-0-0-168 jks]#
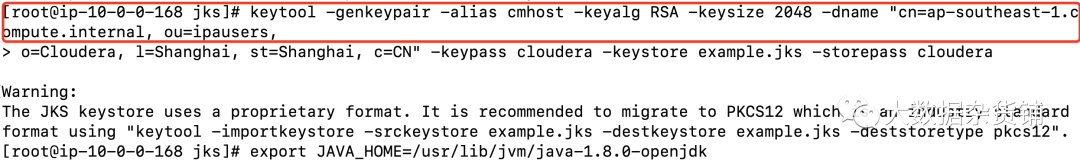
export JAVA_HOME=/usr/lib/jvm/java-1.8.0-openjdksource /etc/profilesudo cp $JAVA_HOME/jre/lib/security/cacerts $JAVA_HOME/jre/lib/security/jssecacerts

keytool -export -alias cmhost -keystore example.jks -rfc -file selfsigned.cer
[root@ip-10-0-0-168 jks]# keytool -export -alias cmhost -keystore example.jks -rfc -file selfsigned.cerEnter keystore password:Certificate stored in file <selfsigned.cer>Warning:The JKS keystore uses a proprietary format. It is recommended to migrate to PKCS12 which is an industry standard format using "keytool -importkeystore -srckeystore example.jks -destkeystore example.jks -deststoretype pkcs12".[root@ip-10-0-0-168 jks]#
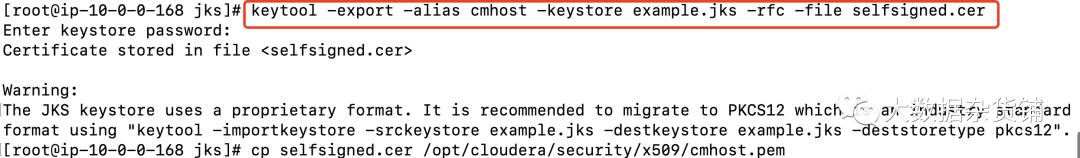
cp selfsigned.cer /opt/cloudera/security/x509/cmhost.pem
$ keytool -import -alias cmhost -file /opt/cloudera/security/jks/selfsigned.cer-keystore $JAVA_HOME/jre/lib/security/jssecacerts -storepass changeit[root@ip-10-0-0-168 jks]# keytool -import -alias cmhost -file /opt/cloudera/security/jks/selfsigned.cerEnter keystore password:Re-enter new password:Owner: CN=ap-southeast-1.compute.internal, OU=ipausers, O=Cloudera, L=Shanghai, ST=Shanghai, C=CNIssuer: CN=ap-southeast-1.compute.internal, OU=ipausers, O=Cloudera, L=Shanghai, ST=Shanghai, C=CNSerial number: 33f6581eValid from: Sun Jul 19 06:07:24 UTC 2020 until: Sat Oct 17 06:07:24 UTC 2020Certificate fingerprints:MD5: 41:C5:94:8B:32:D2:95:67:1D:A2:12:75:6E:05:22:E0SHA1: 8B:BE:F7:7F:75:A0:9B:55:0E:A7:6C:6E:2D:CD:32:CB:79:41:9C:EFSHA256: 54:ED:FE:C2:FA:89:27:DC:3B:06:27:5C:EA:FB:93:2A:8B:A4:6B:27:4A:6E:13:DF:36:DB:76:E9:DE:33:10:55Signature algorithm name: SHA256withRSASubject Public Key Algorithm: 2048-bit RSA keyVersion: 3Extensions:#1: ObjectId: 2.5.29.14 Criticality=falseSubjectKeyIdentifier [KeyIdentifier [0000: 6F C9 8E D3 60 A8 EA 33 BB 44 01 C8 34 5C 14 B1 o...`..3.D..4..0010: E9 CF 6D 1C ..m.]]Trust this certificate? [no]: yesCertificate was added to keystore[root@ip-10-0-0-168 jks]#
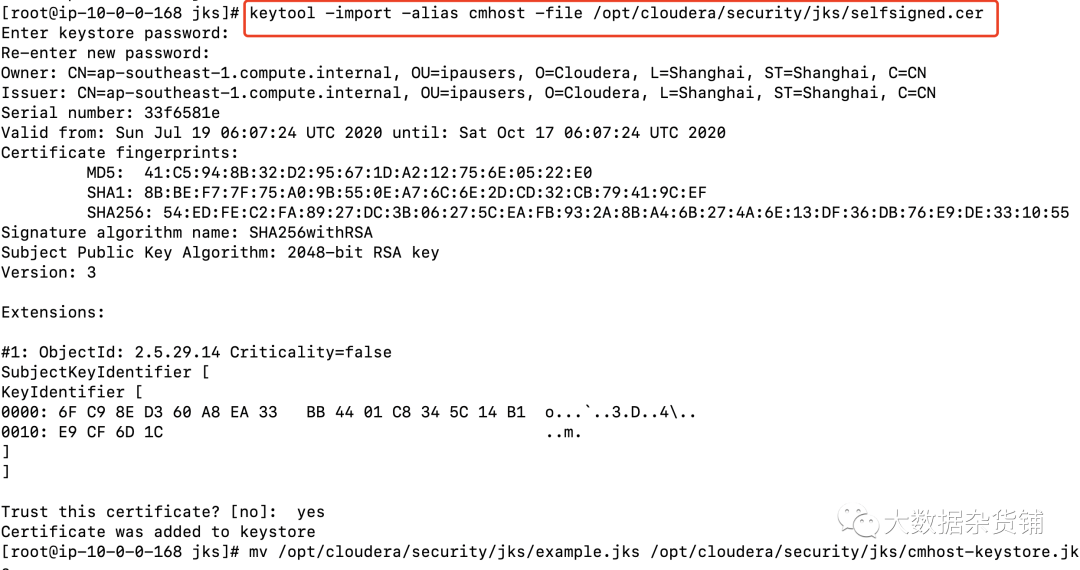
mv /opt/cloudera/security/jks/example.jks /opt/cloudera/security/jks/cmhost-keystore.jks
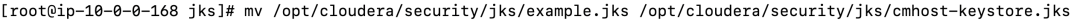
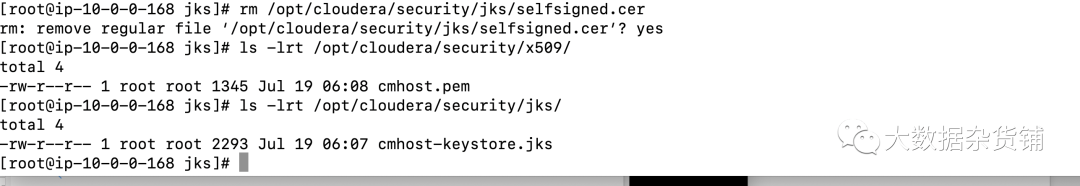
rm /opt/cloudera/security/jks/selfsigned.cer
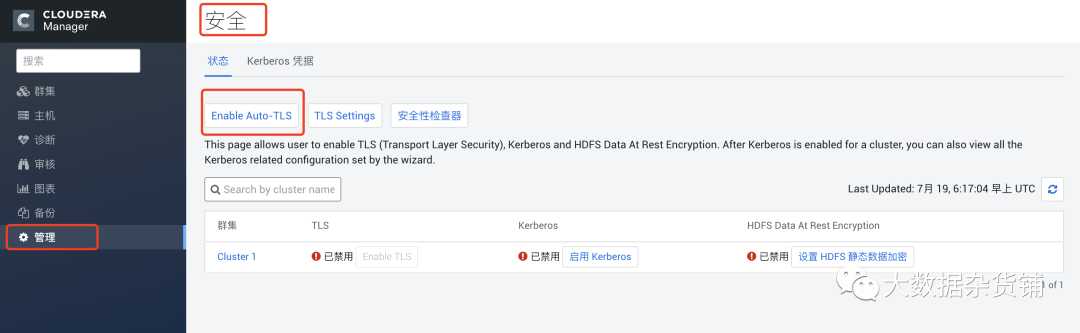
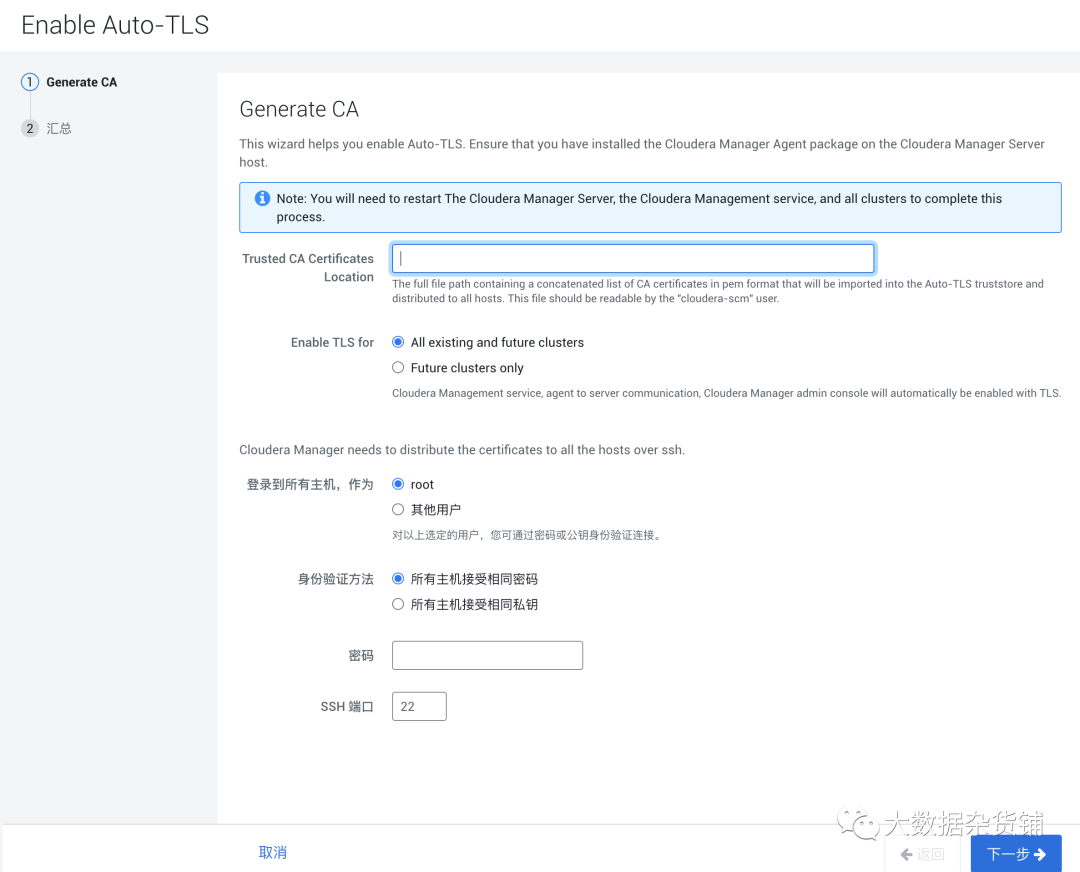
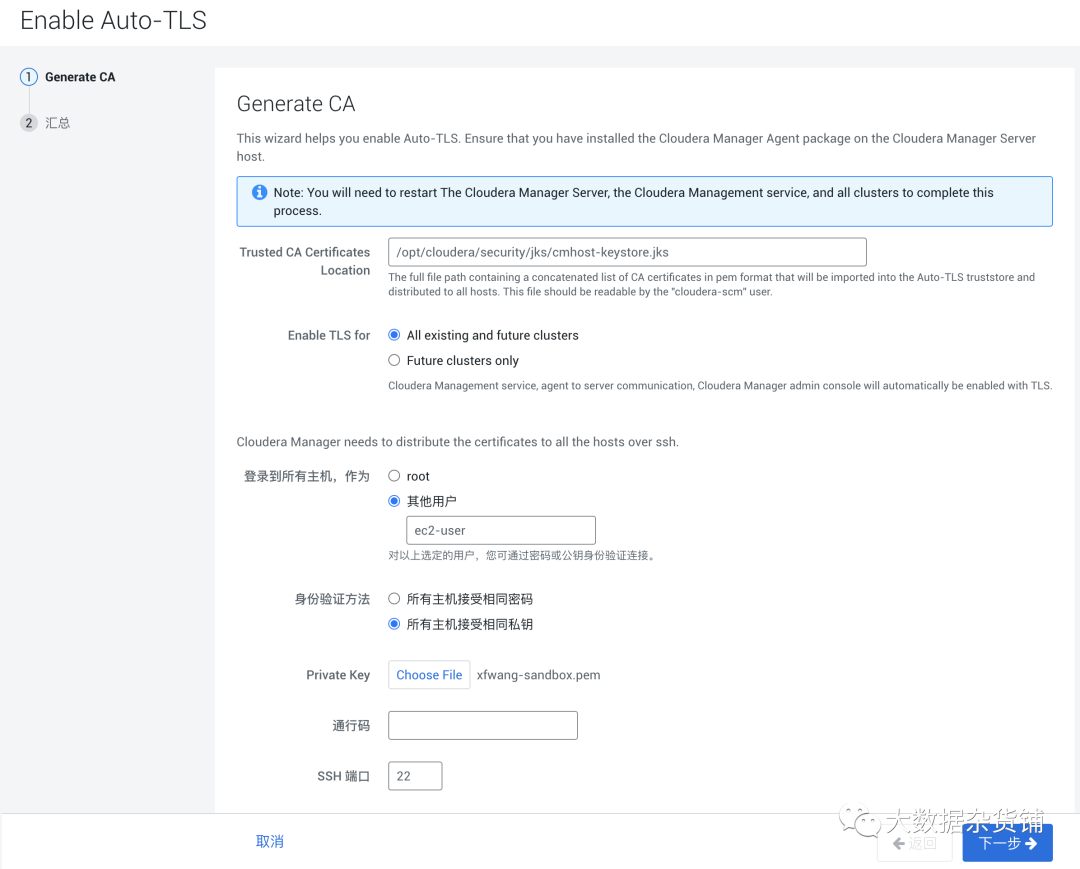
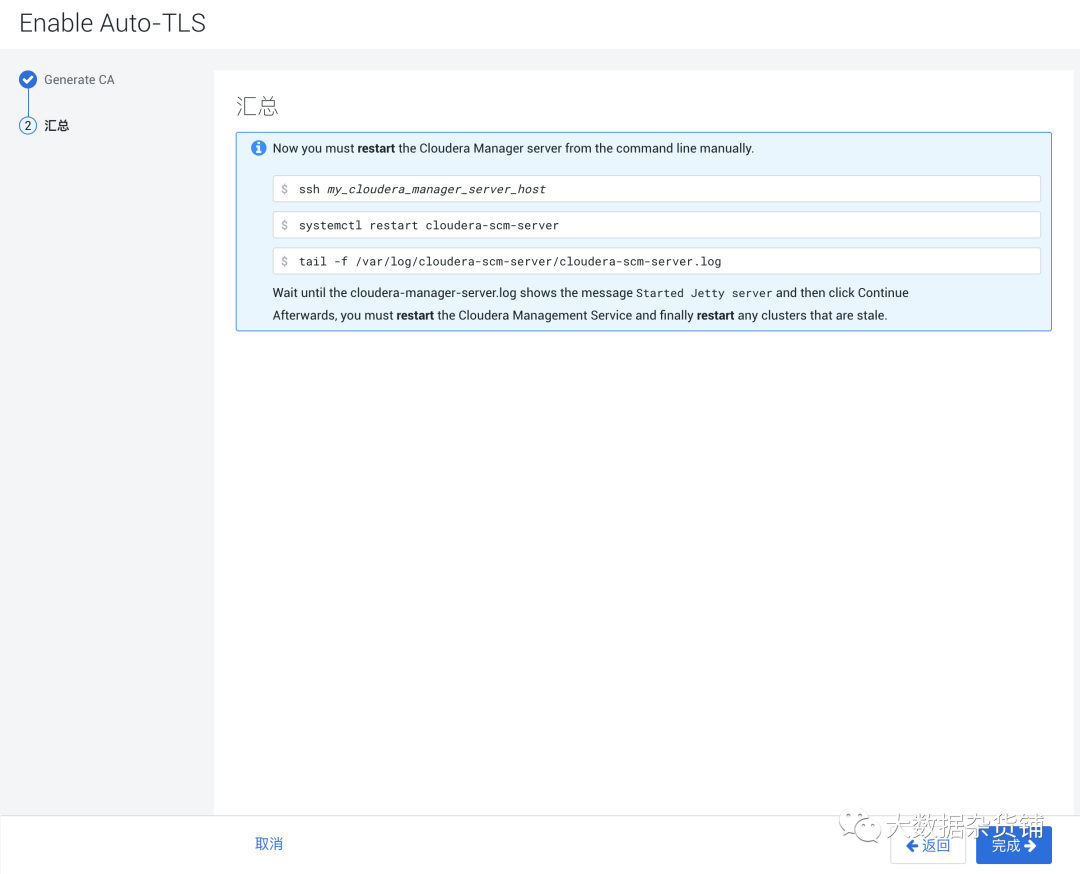
systemctl restart cloudera-scm-server
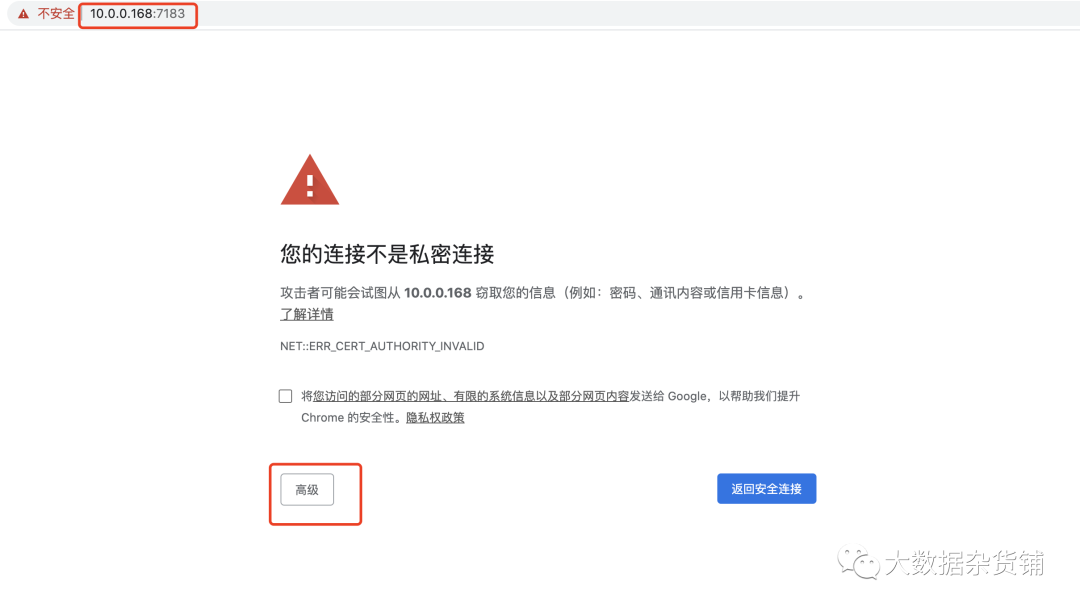

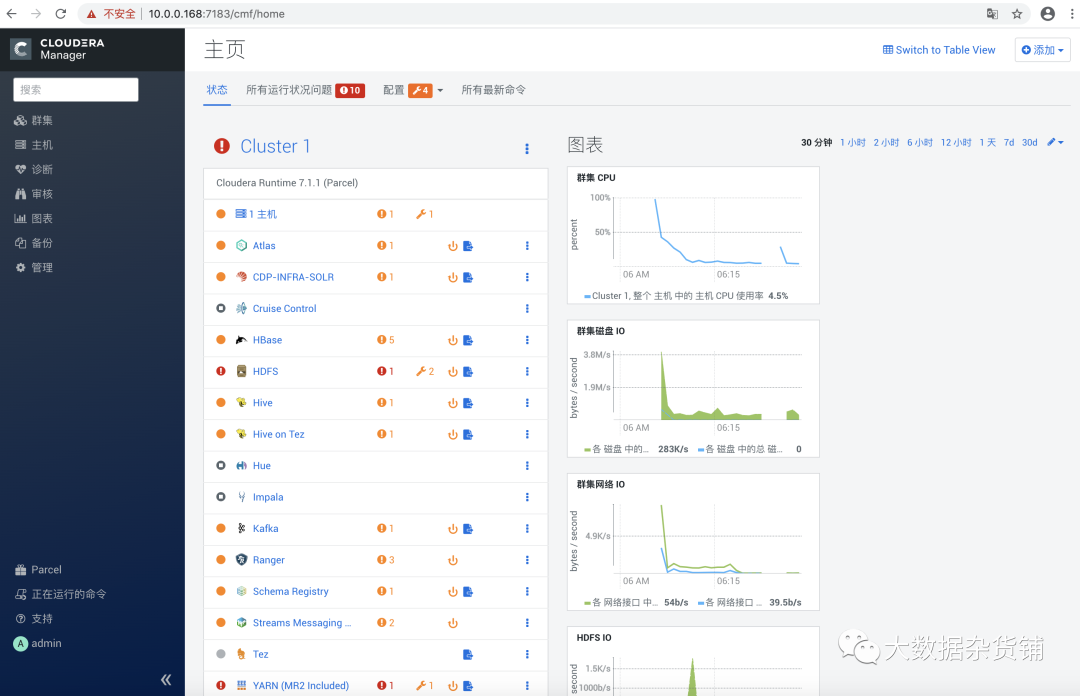
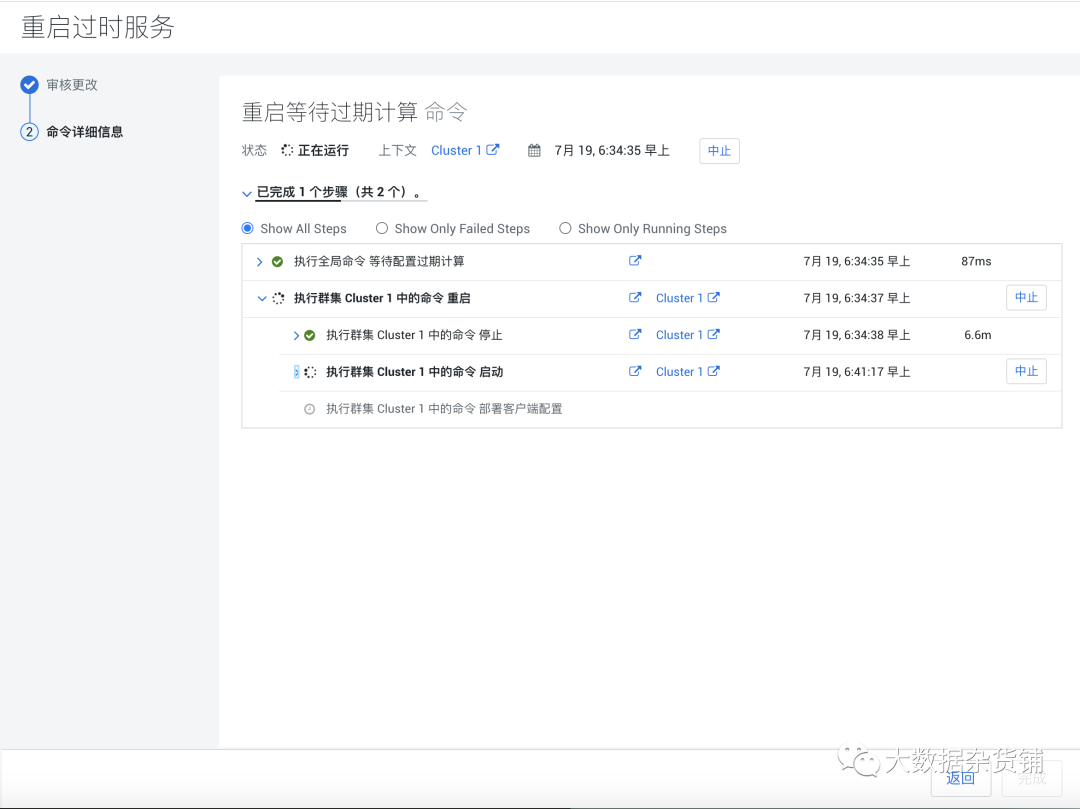
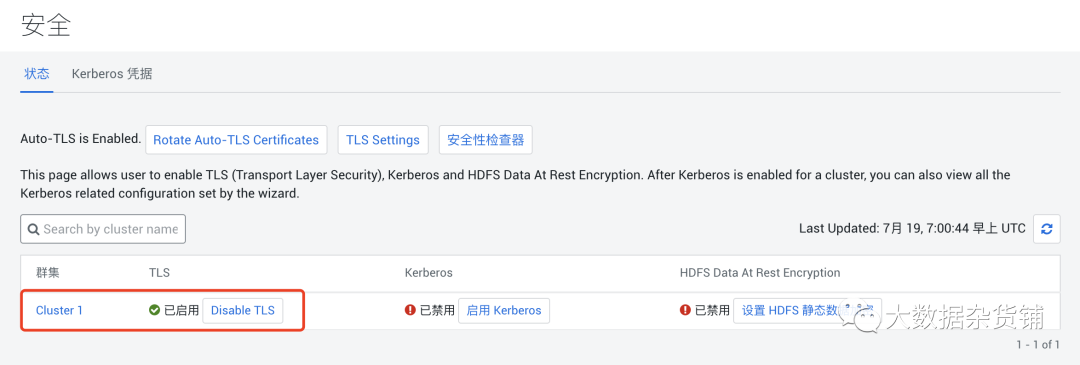

關于現有CDP-DC集群怎么啟用Auto-TLS就分享到這里了,希望以上內容可以對大家有一定的幫助,可以學到更多知識。如果覺得文章不錯,可以把它分享出去讓更多的人看到。
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。