您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
如何進行GitLab實現端到端DevOps流水線實踐,很多新手對此不是很清楚,為了幫助大家解決這個難題,下面小編將為大家詳細講解,有這方面需求的人可以來學習下,希望你能有所收獲。
基于Gitlab實現項目端到端交付實踐,從需求開發開始到交付流水線實現應用發布。每個項目團隊的工作流都是不一樣的,本文檔中的工作流是根據之前項目團隊工作模式而配置的。重點參考技術的實現方式,工作流可以根據自身團隊情況而定義。
來源:http://www.idevops.site
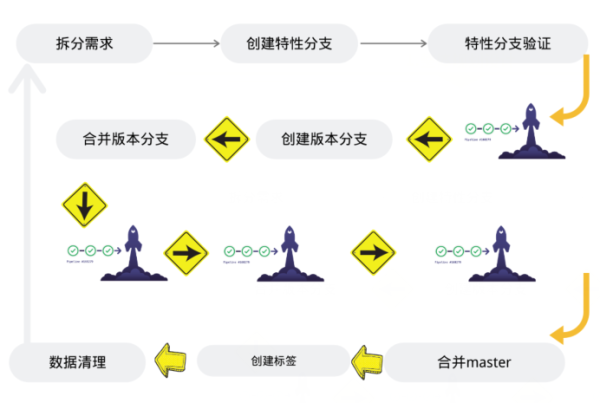
創建issue --> 創建特性分支 --> 特性分支提交流水線 --> 合并分支流水線 --> 發布分支流水線
鴻蒙官方戰略合作共建——HarmonyOS技術社區
創建issues關聯特性分支 (特征以數字開頭的分支為特性分支)
特性分支提交代碼,觸發提交流水線(構建驗證部署到特性環境)
特性環境驗證完成,合并到RELEASE分支。(觸發合并流水線進行代碼掃描,流水線成功才能合并)
RELEASE分支手動發布 (UAT,STAG,PROD)
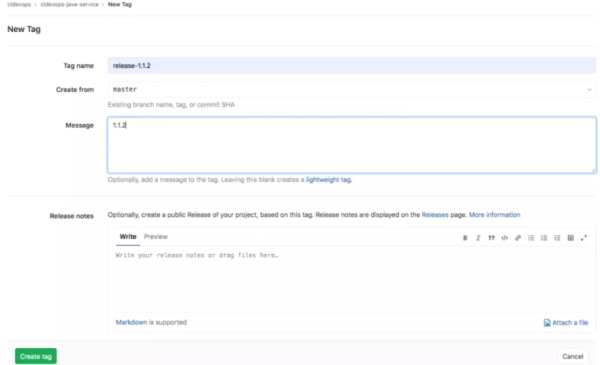
生產發布完成后RELEASE分支合并到Master分支,并基于master分支創建Release tag。
創建里程碑

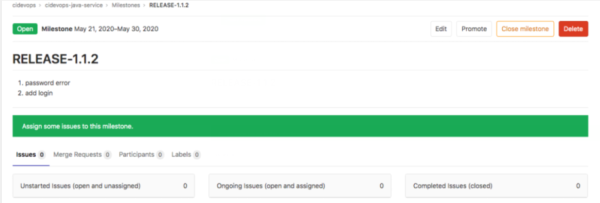
創建issue,關聯里程碑
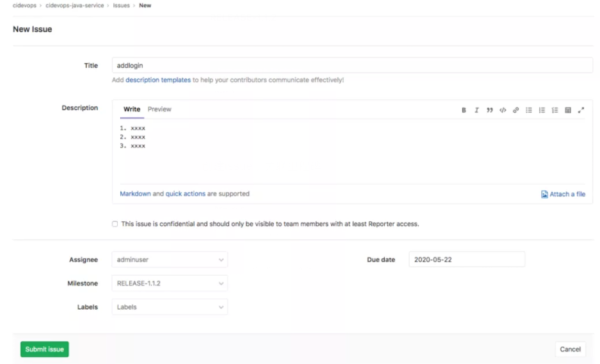
根據issue名稱創建對應的特性分支
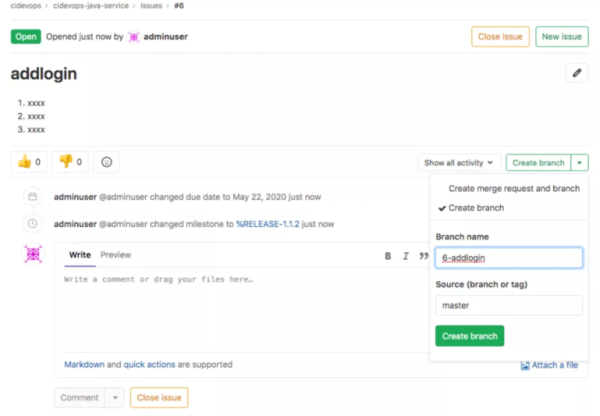
還可以直接使用之前的java項目
github :https://github.com/zeyangli/gitlabci-cidevops-java-service
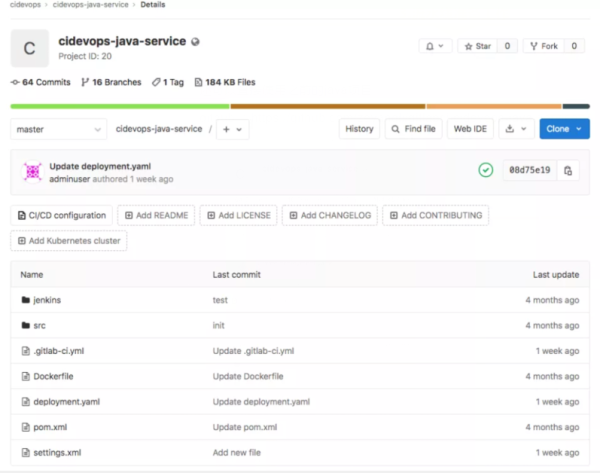
準備模板庫
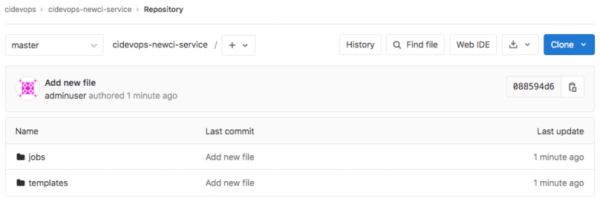
準備可用的runner,根據之前內容安裝部署runner 。
chart :https://github.com/zeyangli/gitlabci-runner-chart-k8s
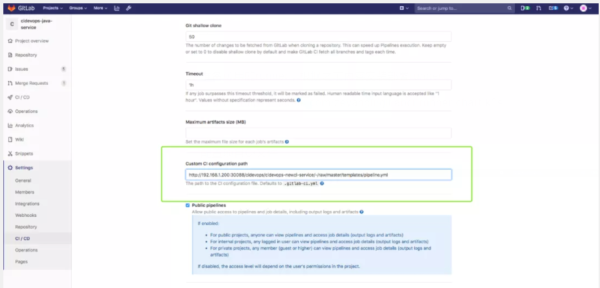
配置項目CI文件
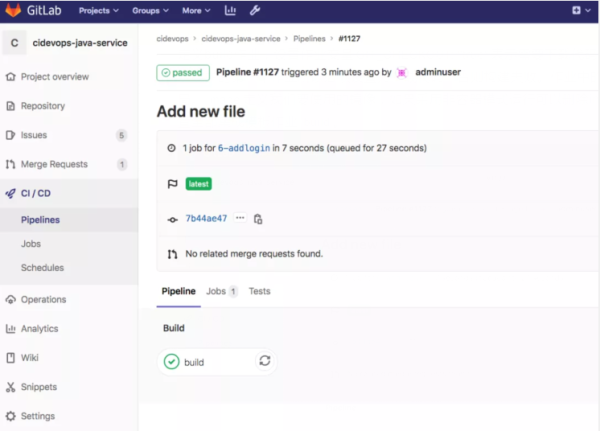
開發人員在特性分支提交代碼,觸發提交流水線進行代碼驗證并發布到特性環境驗證(可手動控制發布)。
階段:編譯,測試,掃描,構建鏡像,上傳鏡像,發布特性環境
特性環境:命名規范為項目名稱-ID-分支名稱,每個特性分支發布到對應的特性環境。
鏡像名稱:
registry.cn-beijing.aliyuncs.com/cidevops/cidevops-java-service:3-input-error-a486c590-834
ingress域名:
"http://${CI_COMMIT_REF_NAME}.${CI_PROJECT_NAMESPACE}.${CI_PROJECT_NAME}.devops.com"定義build作業模板,參數化構建命令。
## build相關作業 ## .build: stage: build script: - ${BUILD_SHELL}在template中引入build作業模板,由于使用容器構建所以聲明MAVEN_IMAGE變量定義鏡像名稱。由于之前對構建環境構建目錄持久化,所以定義GIT_CLONE_PATH參數進入指定的構建目錄操作。GIT_CHECKOUT設置全局每個作業無需重復下載代碼。BUILD_SHELL定義構建所需要的命令。定義變量能夠足夠靈活,適合不同項目不同打包命令的場景下。
include: - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/build.yml' variables: ## 全局配置 GIT_CLONE_PATH: $CI_BUILDS_DIR/builds/$CI_PROJECT_NAMESPACE/$CI_PROJECT_NAME/$CI_PIPELINE_ID GIT_CHECKOUT: "false" ## 依賴容器鏡像 BUILD_IMAGE: "maven:3.6.3-jdk-8" ## 構建測試參數 MAVEN_OPTS: "-Dmaven.repo.local=/home/gitlab-runner/ci-build-cache/maven " BUILD_SHELL: 'mvn clean package -DskipTests --settings=./settings.xml ' ##構建命令 ## 運行階段 stages: - build cache: paths: - target/ ################# Jobs Configure ##################### ## 構建作業 build: variables: GIT_CHECKOUT: "true" image: ${BUILD_IMAGE} extends: .build定義build作業,設置作業變量GIT_CHECKOUT: "true"表示需要下載代碼,默認build是我們流水線中的第一個作業所以必須設置為下載代碼,否則構建失敗。作業中的變量優先級高于全局。image定義我們要使用的鏡像,如果采用非容器模式運行可以刪除image標簽。剩下的配置全部集成模板作業.build。
這里定義的是在運行編譯后進行的單元測試。maven項目一般是mvn test,npm項目一般是npm run test等。不同的項目運行單元測試的指令不通,其他部分都差不多。這里以maven項目為例。開始設計maven項目單元測試。
編輯jobs/test.yml文件定義test作業模板。(后續自動化測試等測試相關作業放到此文件)
#單元測試 .test: stage: test script: - $TEST_SHELL artifacts: reports: junit: ${JUNIT_REPORT_PATH}編輯模板文件,添加導入test作業模板。
include: - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/build.yml' - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/test.yml'
在模板文件中添加變量定義。
variables: TEST_SHELL : 'mvn test --settings=./settings.xml ' ##測試命令 JUNIT_REPORT_PATH: 'target/surefire-reports/TEST-*.xml' ##單元測試報告 ## 測試作業 test: image: ${BUILD_IMAGE} extends: .test before_script: - ls - ls target/ 
jobs/code_analysis.yml
##代碼掃描 ## ## ## .code_analysis: variables: GLOBAL_PROJECT_ARGS: "-Dsonar.projectKey=${CI_PROJECT_NAME} -Dsonar.projectName=${CI_PROJECT_NAME} -Dsonar.projectVersion=${CI_COMMIT_REF_NAME} -Dsonar.projectDescription=${CI_PROJECT_TITLE}" GLOBAL_SERVER_ARGS: "-Dsonar.ws.timeout=30 -Dsonar.links.homepage=${CI_PROJECT_URL} -Dsonar.host.url=${SONAR_SERVER_URL} -Dsonar.login=${SONAR_SERVER_LOGIN} -Dsonar.sourceEncoding=UTF-8 " GLOBAL_MR_ARGS: " -Dsonar.pullrequest.key=${CI_MERGE_REQUEST_IID} -Dsonar.pullrequest.branch=${CI_MERGE_REQUEST_SOURCE_BRANCH_NAME} -Dsonar.pullrequest.base=${CI_MERGE_REQUEST_TARGET_BRANCH_NAME} -Dsonar.gitlab.ref_name=${CI_COMMIT_REF_NAME} -Dsonar.gitlab.commit_sha=${CI_COMMIT_SHA} -Dsonar.gitlab.project_id=${CI_PROJECT_PATH} -Dsonar.pullrequest.gitlab.repositorySlug=${CI_PROJECT_ID} " MULTI_BRANCH_ARGS: "-Dsonar.branch.name=${CI_COMMIT_REF_NAME}" stage: code_analysis script: - echo ${GLOBAL_PROJECT_ARGS} ${GLOBAL_SERVER_ARGS} ${SONAR_SCAN_ARGS} ${GLOBAL_MR_ARGS} #sonar-scanner $GLOBAL_PROJECT_ARGS $GLOBAL_SERVER_ARGS $SCAN_JAVA_ARGS - | if [ $CI_PIPELINE_SOURCE == 'merge_request_event' ] then echo "sonar-scanner ${GLOBAL_PROJECT_ARGS} ${GLOBAL_SERVER_ARGS} ${SONAR_SCAN_ARGS} ${GLOBAL_MR_ARGS}" sonar-scanner ${GLOBAL_PROJECT_ARGS} ${GLOBAL_SERVER_ARGS} ${SONAR_SCAN_ARGS} ${GLOBAL_MR_ARGS} else echo "sonar-scanner ${GLOBAL_PROJECT_ARGS} ${GLOBAL_SERVER_ARGS} ${SONAR_SCAN_ARGS}" sonar-scanner ${GLOBAL_PROJECT_ARGS} ${GLOBAL_SERVER_ARGS} ${SONAR_SCAN_ARGS} ${MULTI_BRANCH_ARGS} fi .get_analysis_result: stage: get_analysis_result script: - | SONAR_REPORT_URL=$(grep "ceTaskUrl" .scannerwork/report-task.txt | awk -F = '{OFS="=";print $2,$3}') echo ${SONAR_REPORT_URL} for i in {1..10} do curl -k -u "ee2bcb37deeb6dfe3a07fe08fb529559b00c1b7b":"" ${SONAR_REPORT_URL} -o sonar_result.txt -s grep '"status":"SUCCESS"' sonar_result.txt && SONAR_SCAN_RESULT='SUCCESS' if [ ${SONAR_SCAN_RESULT} == 'SUCCESS' ] then echo "${SONAR_SCAN_RESULT}" SONAR_SCAN_RESULT=SUCCESS break; else SONAR_SCAN_RESULT='ERROR' echo "第$i次獲取結果信息,不是成功狀態,睡眠10秒!" cat sonar_result.txt sleep 10 fi done流水線模板
templates/pipeline.yml
include: - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/build.yml' - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/test.yml' - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/codeanalysis.yml' variables: ## 全局配置 GIT_CLONE_PATH: $CI_BUILDS_DIR/builds/$CI_PROJECT_NAMESPACE/$CI_PROJECT_NAME/$CI_PIPELINE_ID GIT_CHECKOUT: "false" ## 依賴容器鏡像 BUILD_IMAGE: "maven:3.6.3-jdk-8" SONAR_IMAGE: "sonarsource/sonar-scanner-cli:latest" ## 構建測試參數 MAVEN_OPTS: "-Dmaven.repo.local=/home/gitlab-runner/ci-build-cache/maven " BUILD_SHELL: 'mvn clean package -DskipTests --settings=./settings.xml ' ##構建命令 TEST_SHELL : 'mvn test --settings=./settings.xml ' ##測試命令 JUNIT_REPORT_PATH: 'target/surefire-reports/TEST-*.xml' ##單元測試報告 ## 代碼掃描 SONAR_PROJECT_LANG: "JAVA" SONAR_SOURCE_DIR : "src" SONAR_SERVER_URL: "http://192.168.1.200:30090" SONAR_SERVER_LOGIN: "ee2bcb37deeb6dfe3a07fe08fb529559b00c1b7b" SONAR_SCAN_ARGS: "-Dsonar.sources=${SONAR_SOURCE_DIR} -Dsonar.java.binaries=target/classes -Dsonar.java.test.binaries=target/test-classes -Dsonar.java.surefire.report=target/surefire-reports " ## 運行階段 stages: - build - test - parallel01 cache: paths: - target/ ################# Jobs Configure ##################### ## 構建作業 build: variables: GIT_CHECKOUT: "true" image: ${BUILD_IMAGE} extends: .build ## 測試作業 test: image: ${BUILD_IMAGE} extends: .test before_script: - ls - ls target/ ## 代碼掃描 code_analysis: stage: parallel01 image: ${SONAR_IMAGE} extends: .code_analysis 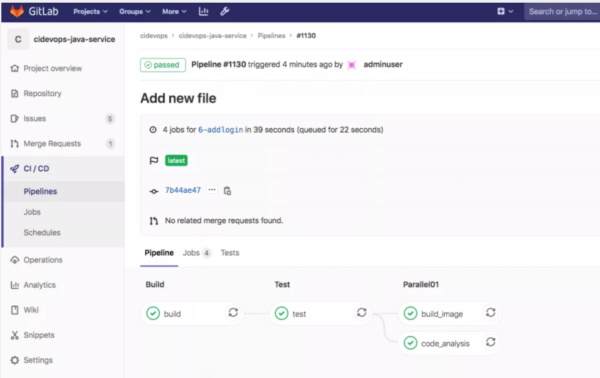
jobs/build.yml
.build-docker: stage: buildimage script: - docker login -u $CI_REGISTRY_USER -p $CI_REGISTRY_PASSWD $CI_REGISTRY - docker build -t ${IMAGE_NAME} -f ${DOCKER_FILE_PATH} . - docker push ${IMAGE_NAME} - docker rmi ${IMAGE_NAME}telmplate/pipeline.yml
include: - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/build.yml' - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/test.yml' - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/codeanalysis.yml' variables: ## 全局配置 GIT_CLONE_PATH: $CI_BUILDS_DIR/builds/$CI_PROJECT_NAMESPACE/$CI_PROJECT_NAME/$CI_PIPELINE_ID GIT_CHECKOUT: "false" ## 依賴容器鏡像 BUILD_IMAGE: "maven:3.6.3-jdk-8" SONAR_IMAGE: "sonarsource/sonar-scanner-cli:latest" ## 構建測試參數 MAVEN_OPTS: "-Dmaven.repo.local=/home/gitlab-runner/ci-build-cache/maven " BUILD_SHELL: 'mvn clean package -DskipTests --settings=./settings.xml ' ##構建命令 TEST_SHELL : 'mvn test --settings=./settings.xml ' ##測試命令 JUNIT_REPORT_PATH: 'target/surefire-reports/TEST-*.xml' ##單元測試報告 ## 代碼掃描 SONAR_PROJECT_LANG: "JAVA" SONAR_SOURCE_DIR : "src" SONAR_SERVER_URL: "http://192.168.1.200:30090" SONAR_SERVER_LOGIN: "ee2bcb37deeb6dfe3a07fe08fb529559b00c1b7b" SONAR_SCAN_ARGS: "-Dsonar.sources=${SONAR_SOURCE_DIR} -Dsonar.java.binaries=target/classes -Dsonar.java.test.binaries=target/test-classes -Dsonar.java.surefire.report=target/surefire-reports " #構建鏡像 CI_REGISTRY: 'registry.cn-beijing.aliyuncs.com' CI_REGISTRY_USER: 'xxxxx' #CI_REGISTRY_PASSWD: 'xxxxxxxx.' IMAGE_NAME: "$CI_REGISTRY/$CI_PROJECT_PATH:$CI_COMMIT_REF_NAME-$CI_COMMIT_SHORT_SHA" DOCKER_FILE_PATH: "./Dockerfile" ## 運行階段 stages: - build - test - parallel01 cache: paths: - target/ ################# Jobs Configure ##################### ## 構建作業 build: variables: GIT_CHECKOUT: "true" image: ${BUILD_IMAGE} extends: .build ## 測試作業 test: image: ${BUILD_IMAGE} extends: .test before_script: - ls - ls target/ ## 代碼掃描 code_analysis: stage: parallel01 image: ${SONAR_IMAGE} extends: .code_analysis ## 構建鏡像 build_image: image: docker:latest services: - name: docker:dind stage: parallel01 extends: .build-docker 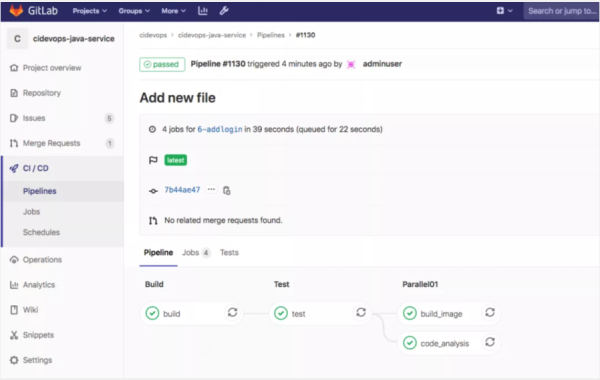
jobs/deploy.yml
## 應用發布 ## 使用kubectl鏡像發布 .deploy_k8s: stage: deploy script: - echo $KUBE_TOKEN - kubectl config set-cluster my-cluster --server=${KUBE_URL} --certificate-authority="${KUBE_CA_PEM_FILE}" - kubectl config set-credentials admin --token=${KUBE_TOKEN} - ls -a - sed -i "s#__namespace__#${NAMESPACE}#g" deployment.yaml - sed -i "s#__appname__#${APP_NAME}#g" deployment.yaml - sed -i "s#__containerport__#${CONTAINER_PORT}#g" deployment.yaml - sed -i "s#__nodeport__#${NODE_PORT}#g" deployment.yaml - sed -i "s#__imagename__#${IMAGE_NAME}#g" deployment.yaml - sed -i "s#__CI_ENVIRONMENT_SLUG__#${CI_ENVIRONMENT_SLUG}#g" deployment.yaml - sed -i "s#__CI_PROJECT_PATH_SLUG__#${CI_PROJECT_PATH_SLUG}#g" deployment.yaml - sed -i "s#__ingressdomain__#${ENV_URL}#g" deployment.yaml - cat deployment.yaml - "kubectl create secret docker-registry ${APP_NAME} \ --docker-server=${CI_REGISTRY} \ --docker-username=$CI_REGISTRY_USER \ --docker-password=${CI_REGISTRY_PASSWD} \ --docker-email=test@test.com -n ${NAMESPACE} || echo 'secrets already exists'" - kubectl apply -f deployment.yaml environment: name: "${CI_COMMIT_REF_NAME}" url: "http://${CI_COMMIT_REF_NAME}.${CI_PROJECT_NAMESPACE}.${CI_PROJECT_NAME}.devops.com" on_stop: rollout_k8s when: manual ## 回滾 .rollout_k8s: stage: rollout script: - rm -rf $HOME/.kube - kubectl config set-cluster my-cluster --server=${KUBE_URL} --certificate-authority="${KUBE_CA_PEM_FILE}" - kubectl config set-credentials admin --token=${KUBE_TOKEN} - kubectl rollout history deployment ${APP_NAME} -n ${NAMESPACE} - kubectl rollout undo deployment ${APP_NAME} -n ${NAMESPACE} when: manual environment: name: "${CI_COMMIT_REF_NAME}" action: stoptemplates/pipeline.yml
include: - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/build.yml' - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/test.yml' - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/codeanalysis.yml' - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/deploy.yml' variables: ## 全局配置 GIT_CLONE_PATH: $CI_BUILDS_DIR/builds/$CI_PROJECT_NAMESPACE/$CI_PROJECT_NAME/$CI_PIPELINE_ID GIT_CHECKOUT: "false" ## 依賴容器鏡像 BUILD_IMAGE: "maven:3.6.3-jdk-8" SONAR_IMAGE: "sonarsource/sonar-scanner-cli:latest" ## 構建測試參數 MAVEN_OPTS: "-Dmaven.repo.local=/home/gitlab-runner/ci-build-cache/maven " BUILD_SHELL: 'mvn clean package -DskipTests --settings=./settings.xml ' ##構建命令 TEST_SHELL : 'mvn test --settings=./settings.xml ' ##測試命令 JUNIT_REPORT_PATH: 'target/surefire-reports/TEST-*.xml' ##單元測試報告 ## 代碼掃描 SONAR_PROJECT_LANG: "JAVA" SONAR_SOURCE_DIR : "src" SONAR_SERVER_URL: "http://192.168.1.200:30090" SONAR_SERVER_LOGIN: "ee2bcb37deeb6dfe3a07fe08fb529559b00c1b7b" SONAR_SCAN_ARGS: "-Dsonar.sources=${SONAR_SOURCE_DIR} -Dsonar.java.binaries=target/classes -Dsonar.java.test.binaries=target/test-classes -Dsonar.java.surefire.report=target/surefire-reports " #構建鏡像 CI_REGISTRY: 'registry.cn-beijing.aliyuncs.com' CI_REGISTRY_USER: 'xxxxx' #CI_REGISTRY_PASSWD: 'xxxxxxxx.' IMAGE_NAME: "$CI_REGISTRY/$CI_PROJECT_PATH:$CI_COMMIT_REF_NAME-$CI_COMMIT_SHORT_SHA" DOCKER_FILE_PATH: "./Dockerfile" #部署應用k8s RUN_DEPLOY: "yes" APP_NAME: "$CI_PROJECT_NAME" CONTAINER_PORT: 8081 #NODE_PORT: 30185 NAMESPACE: "$CI_PROJECT_NAME-$CI_PROJECT_ID-$CI_ENVIRONMENT_SLUG" ## 運行階段 stages: - build - test - parallel01 - deploy - rollout cache: paths: - target/ ################# Jobs Configure ##################### ## 構建作業 build: variables: GIT_CHECKOUT: "true" image: ${BUILD_IMAGE} extends: .build ## 測試作業 test: image: ${BUILD_IMAGE} extends: .test before_script: - ls - ls target/ ## 代碼掃描 code_analysis: stage: parallel01 image: ${SONAR_IMAGE} extends: .code_analysis ## 構建鏡像 build_image: image: docker:latest services: - name: docker:dind stage: parallel01 extends: .build-docker ## 發布應用 deploy_k8s: stage: deploy image: lucj/kubectl:1.17.2 extends: .deploy_k8s ## 應用回滾 rollout_k8s: stage: rollout image: lucj/kubectl:1.17.2 extends: .rollout_k8s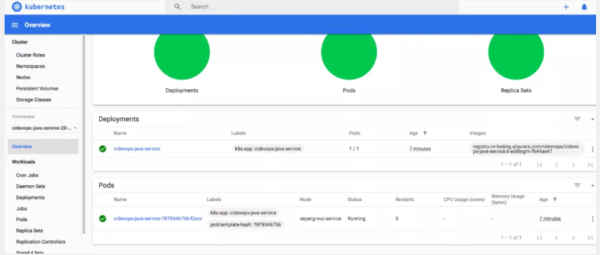
使用workflow:rules 進行流水線控制,我們會用到Pipeline的變量,通過變量限制條件。
預定義變量參考文檔:https://docs.gitlab.com//12.9/ee/ci/variables/predefined_variables.html
變量匹配語法: https://docs.gitlab.com//12.9/ee/ci/variables/README.html#supported-syntax
re2語法:https://github.com/google/re2/wiki/Syntax
運行流水線您會發現,所有新創建的分支的CI_COMMIT_BEFORE_SHA為40個0。
$ export
declare -x CI_BUILD_BEFORE_SHA="0000000000000000000000000000000000000000"
declare -x CI_COMMIT_BEFORE_SHA="0000000000000000000000000000000000000000"
## 流水線控制 workflow: rules: - if: $CI_COMMIT_BEFORE_SHA == "0000000000000000000000000000000000000000" when: never - when: always
如何匹配特性分支和版本分支呢?
#$CI_COMMIT_REF_NAME =~ /\d-*/ #$CI_COMMIT_REF_NAME =~ /^RELEASE-*/ ||
大家可以想像一下,如果是一個剛剛開始關注代碼質量的團隊,避免不了出現代碼質量閾失敗。 改進初期出現錯誤很正常,如果在初期就把質量閾配置的很嚴格,這會導致每次提交代碼都會產生錯誤。所以我們可以適當的放開流水線的代碼掃描(也就是流水線暫時不進行質量閾檢查)。
如果不掃描就無法知道代碼的準確質量,所以我們準備流水線僅掃描但不檢查質量閾,而合并流水線會將代碼質量展示在評論區。類似于這種情況我們可以設置流水線成功后才能合并。
默認是提交觸發流水線運行,而設置了"流水線成功后合并"會檢查原分支的最后一次提交的狀態是否為success,如果是success則運行合并。 我們配置流水線在出現合并請求的時候,進行代碼驗證。
## 流水線控制 workflow: rules: - if: $CI_MERGE_REQUEST_ID
我們將應用的部署文件也存儲在代碼庫中管理,可能每個應用在各個環境中的配置文件不一致。所有分為三個配置文件 deployment-uat.yml、 deployment-stag.yml、 deployment-prod.yml
jobs/deploy.yml
## 應用發布 ## 使用kubectl鏡像發布 .deploy_k8s: stage: deploy script: - echo $KUBE_TOKEN - kubectl config set-cluster my-cluster --server=${KUBE_URL} --certificate-authority="${KUBE_CA_PEM_FILE}" - kubectl config set-credentials admin --token=${KUBE_TOKEN} - ls -a - sed -i "s#__namespace__#${NAMESPACE}#g" ${DEPLOY_FILE} - sed -i "s#__appname__#${APP_NAME}#g" ${DEPLOY_FILE} - sed -i "s#__containerport__#${CONTAINER_PORT}#g" ${DEPLOY_FILE} - sed -i "s#__nodeport__#${NODE_PORT}#g" ${DEPLOY_FILE} - sed -i "s#__imagename__#${IMAGE_NAME}#g" ${DEPLOY_FILE} - sed -i "s#__CI_ENVIRONMENT_SLUG__#${CI_ENVIRONMENT_SLUG}#g" ${DEPLOY_FILE} - sed -i "s#__CI_PROJECT_PATH_SLUG__#${CI_PROJECT_PATH_SLUG}#g" ${DEPLOY_FILE} - sed -i "s#__ingressdomain__#${ENV_URL}#g" ${DEPLOY_FILE} - cat ${DEPLOY_FILE} - "kubectl create secret docker-registry ${APP_NAME} \ --docker-server=${CI_REGISTRY} \ --docker-username=$CI_REGISTRY_USER \ --docker-password=${CI_REGISTRY_PASSWD} \ --docker-email=test@test.com -n ${NAMESPACE} || echo 'secrets already exists'" - kubectl apply -f ${DEPLOY_FILE} environment: name: "${ENV_NAME}" url: "http://${ENV_NAME}.${CI_PROJECT_NAMESPACE}.${CI_PROJECT_NAME}.devops.com" on_stop: "${ROLL_NAME}" ## 回滾 .rollout_k8s: stage: deploy script: - rm -rf $HOME/.kube - kubectl config set-cluster my-cluster --server=${KUBE_URL} --certificate-authority="${KUBE_CA_PEM_FILE}" - kubectl config set-credentials admin --token=${KUBE_TOKEN} - kubectl rollout history deployment ${APP_NAME} -n ${NAMESPACE} - kubectl rollout undo deployment ${APP_NAME} -n ${NAMESPACE} environment: name: "${ENV_NAME}" action: stoptemplates/pipeline.yml
include: - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/build.yml' - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/test.yml' - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/codeanalysis.yml' - project: 'cidevops/cidevops-newci-service' ref: master file: 'jobs/deploy.yml' variables: ## 全局配置 GIT_CLONE_PATH: $CI_BUILDS_DIR/builds/$CI_PROJECT_NAMESPACE/$CI_PROJECT_NAME/$CI_PIPELINE_ID GIT_CHECKOUT: "false" ## 依賴容器鏡像 BUILD_IMAGE: "maven:3.6.3-jdk-8" SONAR_IMAGE: "sonarsource/sonar-scanner-cli:latest" ## 構建測試參數 MAVEN_OPTS: "-Dmaven.repo.local=/home/gitlab-runner/ci-build-cache/maven " BUILD_SHELL: 'mvn clean package -DskipTests --settings=./settings.xml ' ##構建命令 TEST_SHELL : 'mvn test --settings=./settings.xml ' ##測試命令 JUNIT_REPORT_PATH: 'target/surefire-reports/TEST-*.xml' ##單元測試報告 ## 代碼掃描 SONAR_PROJECT_LANG: "JAVA" SONAR_SOURCE_DIR : "src" SONAR_SERVER_URL: "http://192.168.1.200:30090" SONAR_SERVER_LOGIN: "ee2bcb37deeb6dfe3a07fe08fb529559b00c1b7b" SONAR_SCAN_ARGS: "-Dsonar.sources=${SONAR_SOURCE_DIR} -Dsonar.java.binaries=target/classes -Dsonar.java.test.binaries=target/test-classes -Dsonar.java.surefire.report=target/surefire-reports " #構建鏡像 CI_REGISTRY: 'registry.cn-beijing.aliyuncs.com' CI_REGISTRY_USER: 'xxxxxx' #CI_REGISTRY_PASSWD: 'xxxxxxxx.' IMAGE_NAME: "$CI_REGISTRY/$CI_PROJECT_PATH:$CI_COMMIT_REF_NAME-$CI_COMMIT_SHORT_SHA" DOCKER_FILE_PATH: "./Dockerfile" #部署應用k8s RUN_DEPLOY: "yes" APP_NAME: "$CI_PROJECT_NAME" CONTAINER_PORT: 8081 #NODE_PORT: 30185 NAMESPACE: "$CI_PROJECT_NAME-$CI_PROJECT_ID-$CI_ENVIRONMENT_SLUG" ## 流水線控制 workflow: rules: - if: $CI_MERGE_REQUEST_ID - if: $CI_PIPELINE_SOURCE == 'web' - if: $CI_COMMIT_BEFORE_SHA == "0000000000000000000000000000000000000000" when: never ## 運行階段 stages: - build - test - parallel01 - get_analysis_result - deploy - rollout cache: paths: - target/ before_script: - export ################# Jobs Configure ##################### ## 構建作業 build: variables: GIT_CHECKOUT: "true" image: ${BUILD_IMAGE} extends: .build ## 測試作業 test: image: ${BUILD_IMAGE} extends: .test before_script: - ls - ls target/ ## 代碼掃描 code_analysis: stage: parallel01 image: ${SONAR_IMAGE} extends: .code_analysis ## 獲取構建結果 get_analysis_result: image: curlimages/curl:7.70.0 extends: .get_analysis_result needs: - code_analysis ## 構建鏡像 build_image: image: docker:latest services: - name: docker:dind stage: parallel01 extends: .build-docker ## feature發布應用 deploy_feature: variables: DEPLOY_FILE: 'deployment.yaml' ENV_NAME: 'feature' stage: deploy image: lucj/kubectl:1.17.2 extends: .deploy_k8s rules: - if: $CI_COMMIT_REF_NAME =~ /^RELEASE-*/ when: never - if: $CI_COMMIT_REF_NAME =~ /\d-*/ when: manual - when: never ## 應用回滾 rollout_feature: stage: rollout image: lucj/kubectl:1.17.2 extends: .rollout_k8s rules: - if: $CI_COMMIT_REF_NAME =~ /^RELEASE-*/ when: never - if: $CI_COMMIT_REF_NAME =~ /\d-*/ when: manual - when: never ## UAT deploy_uat: variables: DEPLOY_FILE: 'config/deployment-uat.yaml' ENV_NAME: 'uat' stage: deploy image: lucj/kubectl:1.17.2 extends: .deploy_k8s rules: - if: $CI_COMMIT_REF_NAME =~ /^RELEASE-*/ when: manual - when: never ## UAT應用回滾 rollout_uat: stage: rollout image: lucj/kubectl:1.17.2 extends: .rollout_k8s rules: - if: $CI_COMMIT_REF_NAME =~ /^RELEASE-*/ when: manual - when: never ## STAG deploy_stag: variables: DEPLOY_FILE: 'config/deployment-stag.yaml' ENV_NAME: 'stag' stage: deploy image: lucj/kubectl:1.17.2 extends: .deploy_k8s rules: - if: $CI_COMMIT_REF_NAME =~ /^RELEASE-*/ when: manual - when: never ## STAG應用回滾 rollout_stag: stage: rollout image: lucj/kubectl:1.17.2 extends: .rollout_k8s rules: - if: $CI_COMMIT_REF_NAME =~ /^RELEASE-*/ when: manual - when: never ## PROD deploy_prod: variables: DEPLOY_FILE: 'config/deployment-prod.yaml' ENV_NAME: 'prod' stage: deploy image: lucj/kubectl:1.17.2 extends: .deploy_k8s rules: - if: $CI_COMMIT_REF_NAME =~ /^RELEASE-*/ when: manual - when: never ## PROD應用回滾 rollout_prod: stage: rollout image: lucj/kubectl:1.17.2 extends: .rollout_k8s rules: - if: $CI_COMMIT_REF_NAME =~ /^RELEASE-*/ when: manual - when: never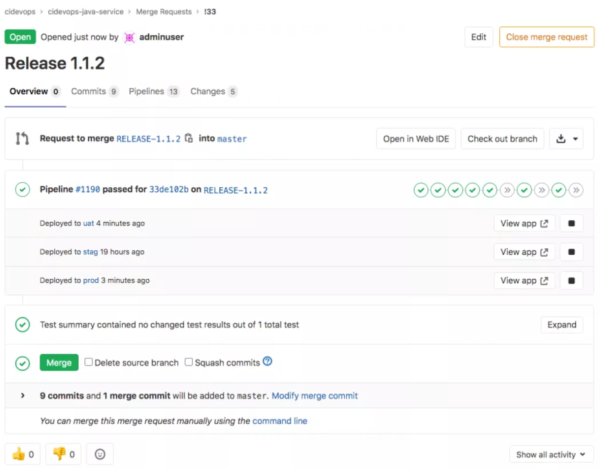

看完上述內容是否對您有幫助呢?如果還想對相關知識有進一步的了解或閱讀更多相關文章,請關注億速云行業資訊頻道,感謝您對億速云的支持。
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。