您好,登錄后才能下訂單哦!
您好,登錄后才能下訂單哦!
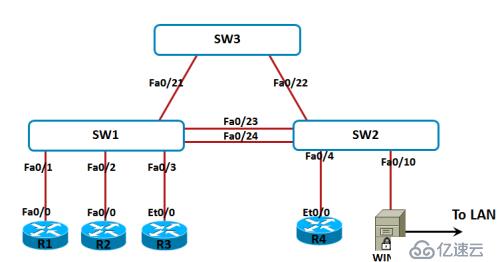
實驗三:DHCP Snooping
1.SW1和SW2上創建VLAN 10,R1-R4劃分到VLAN 10,網段為10.1.1.0/24
2.SW之間的Fa0/24-shutdown;Fa0/23指定成Trunk
3.R4模擬合法的DHCP服務器,在R4上完成DHCP Server的配置
4.R3模擬不合法的DHCP服務器,在R3上完成DHCP Server的配置
5.R1的接口IP設置成DHCP獲得,并且通過show dhcplease查看DHCP Server
6.在SW1上啟用DHCP Snooping,正確配置DHCP snooping,解決此問題.理解DHCP snooping的Trust和untrust的區別.在SW1上查看DHCP Snooping的binding表
7.理解Option82
8.做DHCP限速,SW1的Fa0/1接口每秒最多接收5個DHCP包
R1的配置
R1(config)#int f0/0
R1(config-if)#ip add dhcp
R1(config-if)#no sh
R3的配置
R3(config)#int f0/0
R3(config-if)#ip add 10.10.1.3 255.255.255.0
R3(config-if)#no sh
R3(config)#ip dhcp pool ccie
R3(dhcp-config)#network 10.1.1.0 255.255.255.0
R3(config)#ip dhcp excluded-address 10.1.1.1 10.1.1.50
R4的配置
R4(config)#int e0/0
R4(config-if)#ip add 10.10.1.4 255.255.255.0
R4(config-if)#no sh
R4(config)#ip dhcp pool wolf
R4(dhcp-config)#network 10.1.1.0 255.255.255.0
R4(config)#ip dhcp excluded-address 10.1.1.1 10.1.1.100
SW1的配置
SW1(config)# vlan 10
SW1(config)#int range f0/1 - 3
SW1(config-if)#switchport mode access
SW1(config-if)#switchport access vlan 10
SW1(config)#int ?f0/24
SW1(config-if)#shut
SW1(config)#int ?f0/23
SW1(config-if)#switchport trunk encapsulation dot1q
SW1(config-if)#switchport mode trunk
SW2的配置
SW2(config)# vlan 10
SW2(config)#int e0/4
SW2(config-if)#switchport mode access
SW2(config-if)#switchport access vlan 10
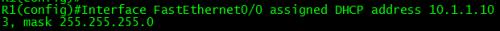
R1#sh dhcp lease
Temp IP addr: 10.1.1.51 ?for peer on Interface: FastEthernet0/0
Temp ?sub net mask: 255.255.255.0
? ?DHCP Lease server: 10.1.1.3, state: 3 Bound
? ?DHCP transaction id: 12B7
? ?Lease: 86400 secs, ?Renewal: 43200 secs, ?Rebind: 75600 secs
? ?Next timer fires after: 11:59:37
? ?Retry count: 0 ? Client-ID: cisco-0002.4b1e.efe0-Fa0/0
#############################################################
SW1(config)# ip dhcp snooping ? // 啟用dhcp snooping功能
SW1(config)# ip dhcp snooping vlan 10
SW1(config)#int f0/23
SW1(config-if)#ip dhcp snooping trust
SW1(config)#no ip dhcp snooping information option ?// 關閉option82
或R4(config)#ip dhcp snooping trust?relay information trust-all // 在DHCP服務器上
? ?//?啟用了DHCP snooping功能的交換機會在discovery消息中添加option82,路由器默認不信任?//?
SW1#sh ip dhcp snooping
Switch DHCP snooping is enabled
DHCP snooping is configured on following VLANs:
10
DHCP snooping is operational on following VLANs:
10
Smartlog is configured on following VLANs:
none
Smartlog is operational on following VLANs:
none
DHCP snooping is configured on the following L3 Interfaces:
Insertion of option 82 is enabled
? ?circuit-id default format: vlan-mod-port
? ?remote-id: 0026.997e.1280 (MAC)
Option 82 on untrusted port is not allowed
Verification of hwaddr field is enabled
Verification of giaddr field is enabled
DHCP snooping trust/rate is configured on the following Interfaces:
Interface ? ? ? ? ? ? ? ? ?Trusted ? ?Allow option ? ?Rate limit (pps)
---------------------- ? ?------- ? ?------------ ? ?---------------- ??
FastEthernet0/23 ? ? ? ? ? yes ? ? ? ?yes ? ? ? ? ? ? unlimit
SW1#sh ip dhcp snooping binding?
MacAddress ? ? ? ? ?IpAddress ? ? ? ?Lease(sec) ?Type ? ? ? ? ? VLAN ?Interface
------------------ ?--------------- ?---------- ?------------- ?---- ?--------------------
00:02:4B:1E:EF:E0 ? 10.1.1.103 ? ? ? 86108 ? ? ? dhcp-snooping ? 10 ? ?FastEthernet0/1
Total number of bindings: 1
SW1(config)#int f0/1
SW1(config-if)#ip dhcp snooping limit rate 5 ?//?限制一秒鐘接收5個DHCP包
免責聲明:本站發布的內容(圖片、視頻和文字)以原創、轉載和分享為主,文章觀點不代表本網站立場,如果涉及侵權請聯系站長郵箱:is@yisu.com進行舉報,并提供相關證據,一經查實,將立刻刪除涉嫌侵權內容。